- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
When I import a Threat Intelligence source that contains an IP address e.g. 1.2.3.4 with weight=60, then another source imports the same IP 1.2.3.4 with weight=100 what happens to the weight?
x
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
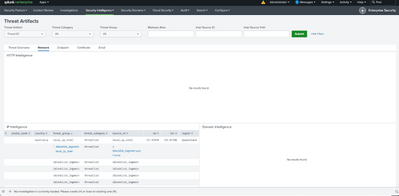
If two Threat Intel Feeds contain the same Object e.g. the IP range 111.221.57.0/24 then the Threat Artefacts Dashboard will recognise this and show the threat_group is multiple sources (screenshots below shows it lists the names in blue)
When Threat Matching queries run, duplicate events will be logged in threat_activity index, one for each threat_group that contains the object.
NOTE: the "Threat Activity Detected" out of the box correlation search dedup's irrespective of weight, so you may want to sort by weight before dedup 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
If two Threat Intel Feeds contain the same Object e.g. the IP range 111.221.57.0/24 then the Threat Artefacts Dashboard will recognise this and show the threat_group is multiple sources (screenshots below shows it lists the names in blue)
When Threat Matching queries run, duplicate events will be logged in threat_activity index, one for each threat_group that contains the object.
NOTE: the "Threat Activity Detected" out of the box correlation search dedup's irrespective of weight, so you may want to sort by weight before dedup 🙂