Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Admin Other
- :
- Security
- :
- Can I get Splunk user activity alerts that include...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Current:
index=_audit user!="splunk-system-user" user!="n/a" user!="MYUSER" user!=testuser* (action="login attempt") OR (search!="" search_id!="'scheduler*" search_id!="scheduler*" search_id!="'subsearch*") | sort - _time | table user host action info search _time
Works well, but many times searches are similar across dashboards and I can't easily tell what dashboard my users are using. Is it possible to add dashboard_name to these alerts? I don't see it anywhere in the _raw for these events in _audit. Currently the only solution I can think of is to mod every back-end search (probably a hundred of them across all my dashboards) with the dashboard name so it can be rexed out... obviously that's an incredibly inelegant approach
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi
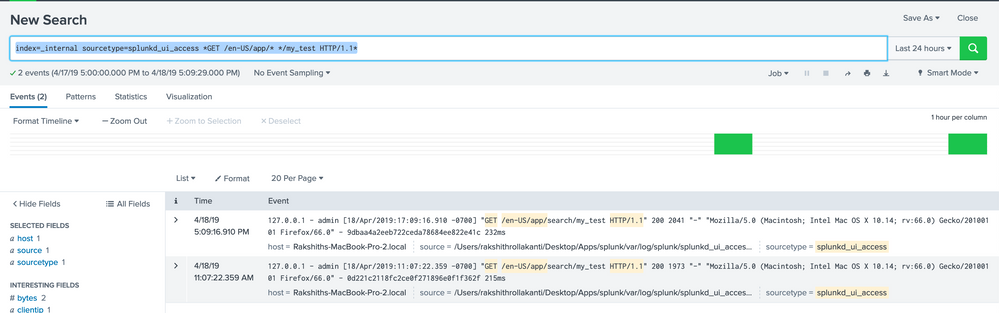
for dashboard usage activity
Please use this search, the results also gives user name as well
in the above search "my_test" is dashboard's name which you see in URL when you open the dashboard.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
GREAT. I modded it to make a bit more usable/readable, and added it to my _audit search, to make my overall user_activity alert be:
(index=_internal sourcetype=splunkd_ui_access uri_path="/en-US/app*") OR (index=_audit AND action="login attempt" OR (search!="" search_id!="'scheduler*" search_id!="scheduler*" search_id!="'subsearch*")) user!="splunk-system-user" user!="n/a" user!="ME" user!=testuser* | eval sortable_time=_time | eval time=strftime(sortable_time,"%Y-%m-%d %H:%M:%S") |
streamstats count as temp_count | stats values(*) as * by temp_count | fields - temp_count | table time user action info search clientip uri_path file earliest latest form_* | fields - _raw form_message_id form_remote_search_tok