Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Administration
- :
- Monitoring Splunk
- :
- Please help me with creating a few Alerts - Share ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please help me with creating a few Alerts - Share SPL please. See message below. Thank u
Please help with SPLs for the following Alerts. Thank u very much in advance.
Active Directory unusual login activity after hours 10PM-6AM EST
Active Directory Possible compromised admin accts
DNS communication with Foreign / Risky countries
SQL DB monitoring unauthorized changes
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Active Directory unusual login activity after hours 10PM-6AM EST
The query that you should use and possible codes that can be related to events in the AD See this post link
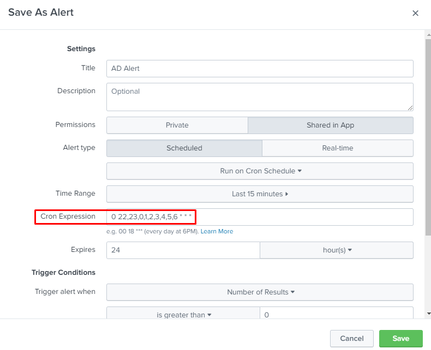
For the non-working time range use this cron when setting the alert after hitting "save as" "alert" Link
0 22,23,0,1,2,3,4,5,6 * * *
Active Directory Possible compromised admin accts
I am sure that in this thread you will find the answer
https://community.splunk.com/t5/All-Apps-and-Add-ons/Example-of-how-to-detect-new-authentication-aga...
DNS communication with Foreign / Risky countries
https://www.splunk.com/en_us/blog/security/hunting-your-dns-dragons.html
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What have you tried so far? Have you checked out the Splunk Security Essentials app? It has examples for similar use cases.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I already have Splunk ES. If that is better that the essential ? Please show me how to use for such Alerts. Thank u
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Enterprise Security and Security Essentials are different apps that do not compete with each other. Use SSE to see examples of what security use cases can be solved with Splunk or ES. It also will help you determine what use cases apply to the data you have and, conversely, what data you need for a given use case.
The SSE app has good documentation that should be reviewed. To see use cases, go to Security Content->Security Content and scroll through what's there.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank u for your message. I am reviewing the Security essentials app. Where is it best to be installed for best output?