- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting an error message as the rule has a malformed related_searches definition?
Hello all,
I am getting an continuous error as the rule has a malformed related_searches definition. i have checked the lookup file as well and everything found normal but i am still getting the error. Is there any inconsistency in the query. The below is the query is used for alerting.
index=wineventlog source="*WinEventLog:Security" EventCode=4688
[
| inputlookup tools.csv WHERE discovery_or_attack=attack
| stats values(filename) as search ]
| transaction host maxpause=5m
| where eventcount>=4
| fields _raw closed_txn field_match_sum linecount
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please share the exact text of the error message and what you are doing when the message appears. Please also share the savedsearches.conf stanza for the correlation search.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
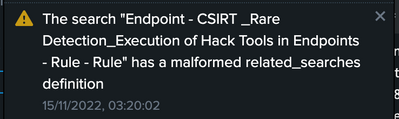
Thank you for the reply.
Please find the error that was displayed frequently in messages column.
and i can't get the savedsearch.conf stanza as we are using the splunk cloud.
Thank you
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If that correlation search was provided by a Splunk app then contact Splunk Cloud Support to have them re-install the app or correct the savedsearches.conf entry.
If this reply helps you, Karma would be appreciated.