Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Getting Data In
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: JSON input: How can I split these values for e...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
wes7bb
New Member
02-14-2018
04:22 AM
Hi there,
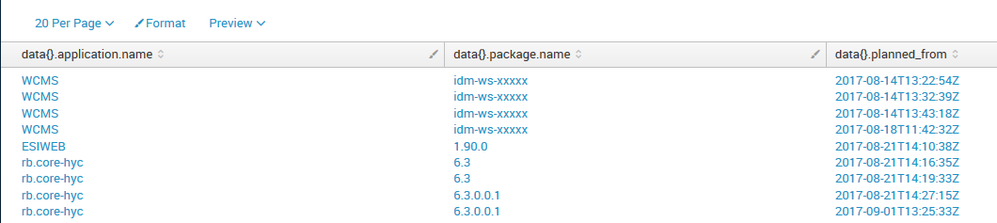
I have a JSON input in Splunk and Splunk extracts the data. But it is not generating for each application in my case WCMS or ESIWEB as their own entry that is possible to sort through this data. All this information is related to one event.
How can I split these values?
I want that for each line break a new row is generated.
Thanks a lot in advance!
Yours
Sina
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
02-14-2018
04:34 AM
@wes7bb ,
Can you please try this?
YOUR_SEARCH
| rename 'data{}.application.name' as 'application_name', 'data{}.package.name' as 'package_name', 'data{}.planned_from' as 'planned_from'
| eval tempField= mvzip(mvzip(application_name,package_name),planned_from)
| stats count by tempField
| eval application_name = mvindex(split(tempField,","),0), package_name= mvindex(split(tempField,","),1), planned_from=mvindex(split(tempField,","),2)
| table application_name package_name planned_from
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
kamlesh_vaghela

SplunkTrust
02-14-2018
04:34 AM
@wes7bb ,
Can you please try this?
YOUR_SEARCH
| rename 'data{}.application.name' as 'application_name', 'data{}.package.name' as 'package_name', 'data{}.planned_from' as 'planned_from'
| eval tempField= mvzip(mvzip(application_name,package_name),planned_from)
| stats count by tempField
| eval application_name = mvindex(split(tempField,","),0), package_name= mvindex(split(tempField,","),1), planned_from=mvindex(split(tempField,","),2)
| table application_name package_name planned_from
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
wes7bb
New Member
02-14-2018
04:53 AM
Thanks a lot for your help! It works!
Get Updates on the Splunk Community!
AI for AppInspect
We’re excited to announce two new updates to AppInspect designed to save you time and make the app approval ...
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...
Operationalizing Entity Risk Score with Enterprise Security 8.3+
Overview
Enterprise Security 8.3 introduces a powerful new feature called “Entity Risk Scoring” (ERS) for ...