Getting Data In
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
- Find Answers
- :
- Splunk Administration
- :
- Getting Data In
- :
- Re: Ingesting Windows Service Status Data
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jamie1
Communicator
03-27-2023
07:47 AM
Hi There,
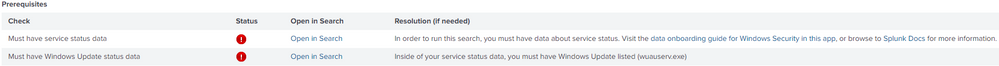
I am new to Splunk and am currently trying to get Windows Services data into Splunk. I am using Splunk Cloud and already have Windows Event Log data being ingested via a Universal Forwarder. I was attempting to make use of a search via Splunk Security Essentials and saw the following:
Unfortunately, when trying to find help online or on Splunk Docs, I only saw solutions about changing inputs.conf. However, as I am on Splunk Cloud, I do not know if this would be possible.
Any help would be appreciated,
Jamie
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
03-27-2023
10:57 AM
The inputs.conf file is on your UF, which you can access.
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
richgalloway

SplunkTrust
03-27-2023
10:57 AM
The inputs.conf file is on your UF, which you can access.
---
If this reply helps you, Karma would be appreciated.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
jamie1
Communicator
03-31-2023
07:46 AM
Hey,
This information helped, thanks man 🙂
Jamie
Get Updates on the Splunk Community!
AppDynamics Summer Webinars
This summer, our mighty AppDynamics team is cooking up some delicious content on YouTube Live to satiate your ...
SOCin’ it to you at Splunk University
Splunk University is expanding its instructor-led learning portfolio with dedicated Security tracks at .conf25 ...
Credit Card Data Protection & PCI Compliance with Splunk Edge Processor
Organizations handling credit card transactions know that PCI DSS compliance is both critical and complex. The ...