- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
danielgp89
Path Finder
01-18-2019
10:07 AM
Hello!
I have events from two different fields that are correlate each other by the time.
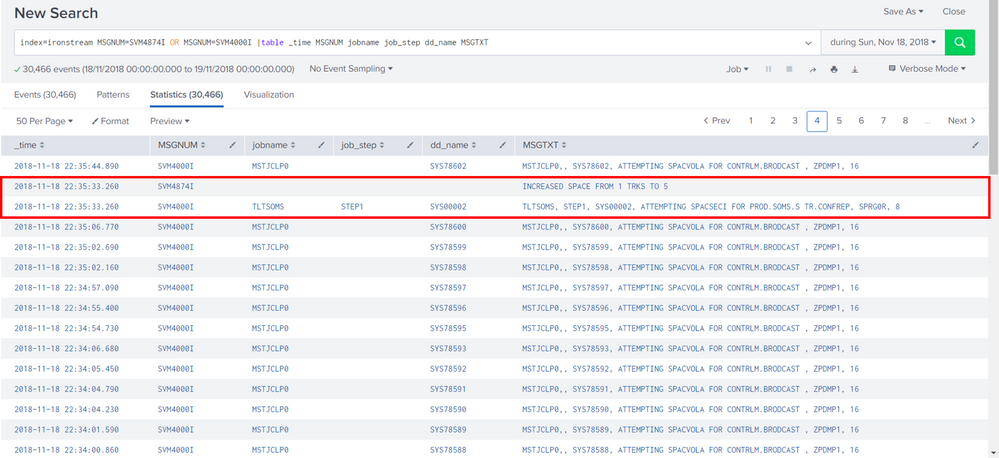
So I want to make a table extracting only those values that were generate at the same time from a range of time of one day.
For example in the table below, there are two values that has the same time:
How can I extract the events that only has the same timestamp from those two fields (MSGNUM=SVM4000I and SVM4874I)
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
01-18-2019
08:43 PM
@danielgp89,
Try this and verify if its working for you
"your base search"|eventstats dc(MSGNUM) as c by _time|where c>1
This should result only those events which has at least 2 MSGNUM values of same time
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
01-18-2019
08:43 PM
@danielgp89,
Try this and verify if its working for you
"your base search"|eventstats dc(MSGNUM) as c by _time|where c>1
This should result only those events which has at least 2 MSGNUM values of same time
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
danielgp89
Path Finder
01-20-2019
06:04 PM
Thanks so much Renjith!
Your going to heaven!