Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- How do you add new field extraction and do proper ...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
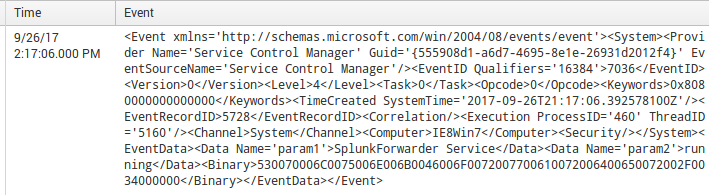
An example of my raw text is attached. How do I do the field extraction and also proper line breaking in event logs like this? I've changed renderXml to true so as to reduce the resource intensity. the sourcetype is XmlWinEventLog
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Question resolved, I changed renderXml to false and proceed using regex (example: rex in splunk) to actually extract fields, this way its much more efficient. In my opinion.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Question resolved, I changed renderXml to false and proceed using regex (example: rex in splunk) to actually extract fields, this way its much more efficient. In my opinion.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Kitteh,
You can install Splunk_TA_Windows add-on (https://splunkbase.splunk.com/app/742/) to extract fields during search time.
Thanks,
Harshil
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Kitteh,
Is this sysmon data?
Thanks,
Harshil
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @harsmarvania57,
No this is not Sysmon data. Particularly on Windows Event Viewer log on application, system and security.
Regards,
Kitteh