Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: Help with dashboard output
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How would I get from the first output to the final output?

- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
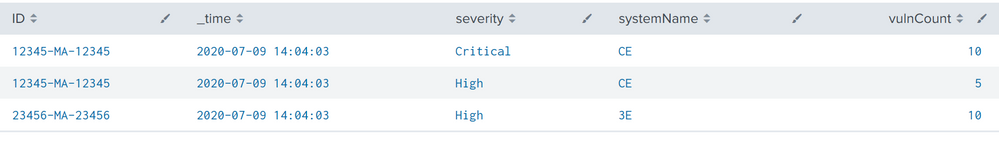
It's not pretty and may not scale far, but this search converts your input into the desired output.
| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="Critical", vulnCount=10
| append
[| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="High", vulnCount=5]
| append
[| makeresults
| eval systemName="3E", ID="23456-MA-23456", severity="High", vulnCount=10]
`comment("Above just creates test data")`
| stats sum(vulnCount) as vulnCount by ID, systemName, severity
`comment("The next two commands reduce the results to 3 fields for xyseries")`
| eval sys=ID."/".systemName
| fields sys, severity, vulnCount
`comment("Re-format the results")`
| xyseries sys severity vulnCount
| fillnull value=0
`comment("The next 2 commands restore the original field names")`
| eval sys=split(sys,"/")
| eval ID=mvindex(sys,0), systemName=mvindex(sys,1)
| table systemName, ID, High, CriticalIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would like to use the data in the first photo (dashboard ) to create the second photo (dashboard).
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
the code for the transition from the first to the last is what I am trying to accomplish.
Displaying systemName, ID total of High and Critical by systemName. I attempted to use eval split function and mvindex but couldn't quite figure it out.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please put the example query into a code block instead of an image so we can paste it into our own Splunk for testing?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I apologize. I don't know how to transform the first photo into the last. I was given the last photo as an example and I am attempting to turn the first photo into the last, that is the reason why I am here. I was hoping that someone would know what it would take to transform the first photo into the last. I do not have the code to do that.
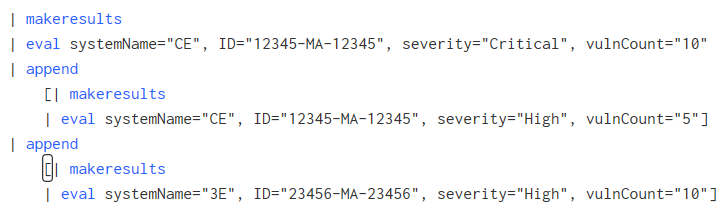
here is the code to the first solution
| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="Critical", vulnCount="10"
| append
[| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="High", vulnCount="5"]
| append
[| makeresults
| eval systemName="3E", ID="23456-MA-23456", severity="High", vulnCount="10"]
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's not pretty and may not scale far, but this search converts your input into the desired output.
| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="Critical", vulnCount=10
| append
[| makeresults
| eval systemName="CE", ID="12345-MA-12345", severity="High", vulnCount=5]
| append
[| makeresults
| eval systemName="3E", ID="23456-MA-23456", severity="High", vulnCount=10]
`comment("Above just creates test data")`
| stats sum(vulnCount) as vulnCount by ID, systemName, severity
`comment("The next two commands reduce the results to 3 fields for xyseries")`
| eval sys=ID."/".systemName
| fields sys, severity, vulnCount
`comment("Re-format the results")`
| xyseries sys severity vulnCount
| fillnull value=0
`comment("The next 2 commands restore the original field names")`
| eval sys=split(sys,"/")
| eval ID=mvindex(sys,0), systemName=mvindex(sys,1)
| table systemName, ID, High, CriticalIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your problem is resolved, then please click an "Accept as Solution" button to help future readers.
If this reply helps you, Karma would be appreciated.