Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Dashboards & Visualizations
- :
- Re: Exclude specific output in XML search
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Exclude specific output in XML search
I am trying to exclude results from a set of data from an XML data source.
I can search for events containing the particular string but when I change the search to "does not equal" it will return no results at all.
In this example, I want to exclude "Card 3 Total Modems" but Splunk will show no results if I change it or by clicking on the field and selecting "exclude results."
source="C:\\Users\\evanr\\splunk\final.xml" host="OSSTEST01" index="prtg_api_cmts" sourcetype="prtg_api" | search "group{@name}"="Twin Valley CMTS" | table _time, group{@name}, group.sensor{@name}, group.sensor.value
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Sorry for the delay, can you give this a go a let me know if this is what you are looking for?
Assumptions:
- Your event has a _raw field with all the XML data in there
- You want to filter group name = "Twin Valley CMTS" but if not simply apply the same logic as below
- You don't want to see "Card 3 Total Modems" but if not simply modify the filter below
- If you want to summarise the final output into values simply use stats values(fieldname) as fieldname to do that
Query:
your base search here
| rex field=_raw "(?msi)(?<group>\<group name=\"Twin Valley CMTS\".+?\</group\>")
| spath input=group
| eval temp = mvzip('group.sensor{@name}', 'group.sensor.value', " <--> ")
| fields - "group.sensor{@name}", "group.sensor.value"
| mvexpand temp
| search temp != "Card 3 Total Modems*"
| rex field=temp "(?<name>.+) \<--\> (?<value>.+)"
| rename name as "group.sensor{@name}", value as "group.sensor.value"
| fields - temp, group, _raw
When I tried this with the sample you attached last week this is what I got (see picture below):
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @evan_roggenkamp please don't forget to mark it as answered if it solved your problem so that we can close this thread and let others benefit from the answer.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you upload "C:\Users\evanr\splunk\final.xml" as we should be able to replicate your problem very easily that way?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
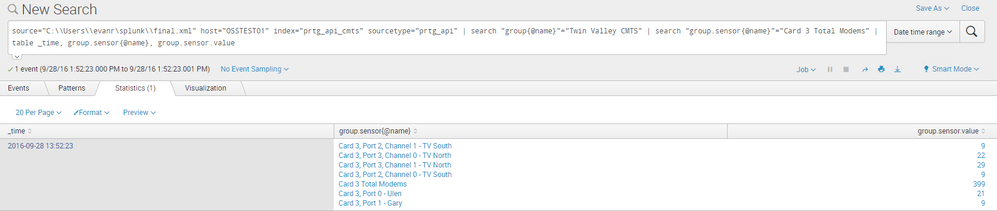
On the image, you are searching for Card 3 Total modems and it is returning only one event. so, if you want to remove that line "Card 3 total modems", the search won't return any events.
I think it's due to the source XML and the line breaking.
May I know, how many events are returned by this query -
source="C:\Users\evanr\splunk\final.xml" host="OSSTEST01" index="prtg_api_cmts" sourcetype="prtg_api" | search "group{@name}"="Twin Valley CMTS" | table _time, group{@name}, group.sensor{@name}, group.sensor.value
Sekar
PS - If this or any post helped you in any way, pls consider upvoting, thanks for reading !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This returns essentially one event, with all of the groups included. It looks exactly like the image above.
Here is the neat thing - this XML file I created with python. So if there is some better way of formatting/structuring the source XML to increase the flexibility I have in Splunk to filter it, I can do that. It is just a matter of updating the python code.
Do you have any recommendations?