Are you a member of the Splunk Community?
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- Re: Microsoft 365 Defender Add-on for Splunk - Doc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Microsoft 365 Defender Add-on for Splunk - Documenation
Does anyone have any information about how to use the new Alert Actions?
We created a simple alert which has output greater than 0, added the account name, and pasted in a simple KQL. Nothing happens
Release Notes
Alert actions introduced:
Advanced Hunting alert action runs advanced hunting queries on entities to ingest additional detail
Incident Update alert action updates the Microsoft 365 Defender portal from a Splunk search
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why we need this add-on? We have a requirement to ingest MCAS logs into splunk (salesforce logs flows into MCAS and those logs from MCAS to be ingested into splunk) Can I use the above add-on to achieve this?
Or should I use Syslog collectors to ingest MCAS logs into splunk?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The incidents and alerts inputs for this add-on work perfectly! We bring them in all day.
The alert_actions do not work very well. We are using the workaround @jconger mentioned below.
We have the makeresults command setup as a scheduled report to bring in custom advanced threat hunting queries.
@jconger - on the next release, could you add a custom KQL input? This would be similar to how TA for Defender ATP hunting API | Splunkbase does this. There is an input to simply run the KQL against defender api. The makeresults command already has the correct structure.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The alert actions are utilized by the workflow actions (check out workflow_actions.conf) and dashboards (check out the incident_detail.xml dashboard). However, the actions can be used independently as well.
Here is an example of using the alert action independently via SPL to hunt based on an IP address:
| makeresults | eval index="YOUR INDEX (defaults to main)", tenant_id="YOUR TENANT ID", query="let ip='IP ADDRESS'; search in (DeviceNetworkEvents, DeviceFileEvents, DeviceLogonEvents, DeviceEvents, EmailEvents, IdentityLogonEvents, IdentityQueryEvents, IdentityDirectoryEvents, CloudAppEvents) Timestamp between (ago(7d) .. now()) and (IPAddress == ip or LocalIP == ip or FileOriginIP == ip or RequestSourceIP == ip or SenderIPv4 == ip or SenderIPv6 == ip or RemoteIP == ip or DestinationIPAddress == ip) | top 100 by Timestamp" | sendalert defender_advanced_huntingThe results will be indexed into whatever index you specified. If you do not include the index in the search, results will go in the main index. The sourcetype will be m365:defender:incident:advanced_hunting.
Search for the results of the hunting action:
index="YOUR INDEX" sourcetype="m365:defender:incident:advanced_hunting"
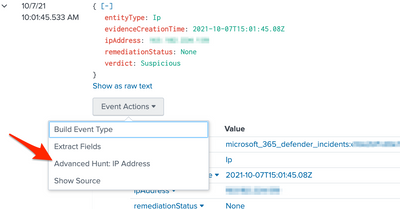
As mentioned, these alert actions are utilized by workflow actions. To observe this, navigate to the Defender 365 Incident Queue dashboard, select an incident (the Incident Detail dashboard should open), select the Entities button in the dashboard, expand the entity, and select Event Actions (see screenshot below). Depending on the entityType field, different actions will appear. Currently, the add-on implements workflow actions for IP addresses, Users, and Files. This can be expanded to other types of entities by editing the workflow_actions.conf file.
Still with me? Okay, because there is a different way to get this hunting data. The workflow actions are ad-hoc hunting queries, but you can continuously export all of this table data to an event hub from Defender. Then, use the Splunk Add-on for Microsoft Cloud Services to ingest the data from the event hub. If you go this route, I suggest installing this add-on that maps all of the Defender event hub data to the Common Information Model (CIM) => https://splunkbase.splunk.com/app/5518/
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
maybe, if you have time from all the .conf questions you have coming in; make an input that only runs the hunting queries?
the only last thing we have is the timestamp recognition. it uses the calling time instead of the Timestamp you have configured.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi jason,
one question about the timestamp parsing using your makeresults command. All the events come in with the exact same _time value.
so we get this when searching
Events might not be returned in sub-second order due to search memory limits. See search.log for more information. Increase the value of the following limits.conf setting:[search]:max_rawsize_perchunk."
Where do you set the timestamp parsing? we tried props, but it did not take affect
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Jason,
Here is a simple KQL which works with makeresults, but not with the alert_action
AlertEvidence | where Timestamp > ago(7d)
| makeresults
| eval index="main", tenant_id="12345-02da-47f3-a903-12345", query="AlertEvidence | where Timestamp > ago(7d)"
| sendalert defender_advanced_hunting param.account_name="MDATP_API_Access" param.global_account_name="MDATP_API_Access"
Next, I look in the logs:
index=cim_modactions source="/opt/splunk/var/log/splunk/defender_advanced_hunting_modalert.log" signature=*
| table _time action_mode signature
| sort - _time
Which brings this result
2021-10-20 08:49:31.570 adhoc Successfully created splunk events
2021-10-20 08:49:30.763 adhoc do_query() - Number of results : 28792
2021-10-20 08:49:10.417 adhoc _Splunk_ Getting proxy server.
2021-10-20 08:49:08.786 adhoc _Splunk_ Defender account name : MDATP_SEAR_API_Access
2021-10-20 08:49:08.774 adhoc _Splunk_ Alert action defender_advanced_hunting started.
2021-10-20 08:49:04.150 adhoc Invoking modular action
Next i added the exact same copy/paste search to a saved search in the alert actionk, Defender Advanced Hunting
2021-10-20 08:50:15.183 saved _Splunk_ Error getting ta_ms_defender_account: 'ta_ms_defender_account'
2021-10-20 08:50:15.177 saved _Splunk_ Alert action defender_advanced_hunting started.
2021-10-20 08:50:10.776 saved Invoking modular action
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
interesting, we now have hundreds of thousands of events in main, but none in the correct index
index=main sourcetype="stash_common_action_model*"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you Jason,
Here is a search we executed:
| makeresults
| eval index="cloud_security_microsoft", tenant_id="<TENANT ID>", query="DeviceEvents | where ActionType == 'AntivirusScanCompleted' | where Timestamp > ago (1h)"
| sendalert defender_advanced_hunting param.account_name="MDATP_API_Access" param.global_account_name="MDATP_API_Access"
This gave us data, but in the main index, and with the incorrect sourcetype
The results are here:
index=main sourcetype="stash_common_action_model-6" InitiatingProcessCreationTime=*
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you have the Common Information Model add-on installed?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Affirmative. Installed on both Heavy Forwarder and search head cluster.
We have continued to run into issues with the alert_action
The Event Hub works well from Defender, the challenge is volume. Our defender data brings in 1.5TB per day into Splunk. The SOC needs the Advanced Threat hunting data along with the incidents and alerts.
We were using Add-on for Defender ATP Hunting API to bring in the Hunting API. However, that stopped working with 8.2.
So we are considering a method to use the Event Hub, and then maybe filter inputs to only what we need. A poor man's threat hunting?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
our setup:
Heavy Forwarder - account setup, and inputs configured to pull Incidents and Alerts
Search Head Cluster - Account name setup there also
SHC - Alert Action with Advanced Hunting set - Test - KQL - Alert
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any information, documents, writeups or examples on how to use these new Alert actions would be incredibly useful. What is the variable format in the Incident Update alert action? I'm assuming $fieldname$? for the Hunting query, do we need to replace the > character with ;gt ?
We have the inputs on a heavy forwarder and the add-on installed on the search head cluster.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is the full log from the last run of the alert:
2021-10-05 18:25:05,937 INFO pid=16772 tid=MainThread file=cim_actions.py:message:431 | sendmodaction - worker="SEARCH-HEAD" signature="Invoking modular action" action_name="defender_advanced_hunting" search_name="Test - KQL - Alert" sid="scheduler_YWRtLWpvaG5ueS5ibGl6emFyZA_VEEtTVNfRGVmZW5kZXI__RMD5e3ec459a641895e9_at_1633458300_871_C0398236-4083-4264-97A9-2408308CBC8C" rid="0" app="TA-MS_Defender" user="splunk-admin-user" digest_mode="1" action_mode="saved"
2021-10-05 18:25:10,336 INFO pid=16772 tid=MainThread file=cim_actions.py:message:431 | sendmodaction - worker="SEARCH-HEAD" signature="_Splunk_ Alert action defender_advanced_hunting started." action_name="defender_advanced_hunting" search_name="Test - KQL - Alert" sid="scheduler_YWRtLWpvaG5ueS5ibGl6emFyZA_VEEtTVNfRGVmZW5kZXI__RMD5e3ec459a641895e9_at_1633458300_871_C0398236-4083-4264-97A9-2408308CBC8C" rid="0" app="TA-MS_Defender" user="splunk-admin-user" digest_mode="1" action_mode="saved" action_status="success"
2021-10-05 18:25:10,343 INFO pid=16772 tid=MainThread file=cim_actions.py:message:431 | sendmodaction - worker="SEARCH-HEAD" signature="_Splunk_ Defender account name : MDATP_SEAR_API_Access" action_name="defender_advanced_hunting" search_name="Test - KQL - Alert" sid="scheduler_YWRtLWpvaG5ueS5ibGl6emFyZA_VEEtTVNfRGVmZW5kZXI__RMD5e3ec459a641895e9_at_1633458300_871_C0398236-4083-4264-97A9-2408308CBC8C" rid="0" app="TA-MS_Defender" user="splunk-admin-user" digest_mode="1" action_mode="saved" action_status="success"
2021-10-05 18:25:10,348 ERROR pid=16772 tid=MainThread file=cim_actions.py:message:431 | sendmodaction - worker="SEARCH-HEAD" signature="get_credentials_with_account_name() - Type 3 - The stanza name None specified is not in the global account configuration. Tested with stanza name : MDATP_SEAR_API_Access. Retrying ... " action_name="defender_advanced_hunting" search_name="Test - KQL - Alert" sid="scheduler_YWRtLWpvaG5ueS5ibGl6emFyZA_VEEtTVNfRGVmZW5kZXI__RMD5e3ec459a641895e9_at_1633458300_871_C0398236-4083-4264-97A9-2408308CBC8C" rid="0" app="TA-MS_Defender" user="splunk-admin-user" digest_mode="1" action_mode="saved" action_status="failure"
2021-10-05 18:25:10,348 ERROR pid=16772 tid=MainThread file=cim_actions.py:message:431 | sendmodaction - worker="SEARCH-HEAD" signature="get_credentials_with_account_name() - Type 3 - Exception occurred. The global account name specified has not been configured. Please re-configure them or re-enter the right stanza name." action_name="defender_advanced_hunting" search_name="Test - KQL - Alert" sid="scheduler_YWRtLWpvaG5ueS5ibGl6emFyZA_VEEtTVNfRGVmZW5kZXI__RMD5e3ec459a641895e9_at_1633458300_871_C0398236-4083-4264-97A9-2408308CBC8C" rid="0" app="TA-MS_Defender" user="splunk-admin-user" digest_mode="1" action_mode="saved" action_status="failure"