Join the Conversation
- Find Answers
- :
- Apps & Add-ons
- :
- All Apps and Add-ons
- :
- How to map to Security Essential hard coded search
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi folks,
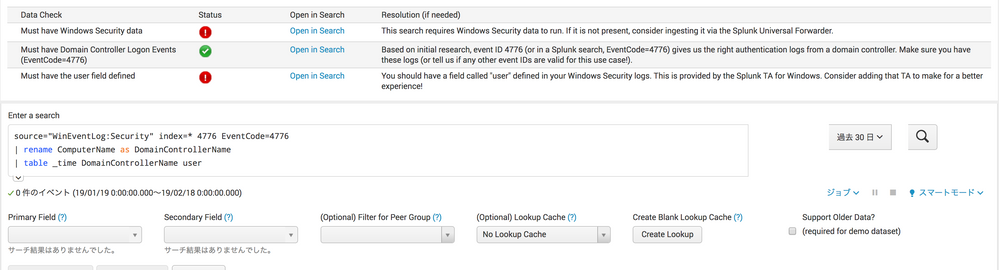
My environment is collecting windows security event and use Splunk Add-on for Microsoft Windows.
Collecting events are indexed with below source and sourcetype.
source=“XmlWinEventLog:Security”
sourcetype=“XmlWinEventLog"
I'd like to confirm my events with security essential app rules but search is based on different source name like below SPL.
Of course, just modify SPL on this page is easy but I'd like to avoid modifying every time to see this page or other windows security based sample searches.
How to change or rename (eval or aliases) source with few step of works?
Thanks,
Satoshi
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I've been told before is that the field extractions for XML Windows Events is non-standard. Outside of sysmon, it's also quite rare.
What I would encourage you to do in these situations is to click Show SPL and then copy-paste the SPL (or click Open in Search) and then adapt fields or sourcetypes as appropriate for your situation. We absolutely want to make this process easier in general, but there are some pretty big technology challenges to making this totally generalizable. It's something still in the queue though, in the hopes of being able to make it happen at some point!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What I've been told before is that the field extractions for XML Windows Events is non-standard. Outside of sysmon, it's also quite rare.
What I would encourage you to do in these situations is to click Show SPL and then copy-paste the SPL (or click Open in Search) and then adapt fields or sourcetypes as appropriate for your situation. We absolutely want to make this process easier in general, but there are some pretty big technology challenges to making this totally generalizable. It's something still in the queue though, in the hopes of being able to make it happen at some point!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is it correct to say at this time that we should add renderXml=false to the stanzas in local/inputs.conf for Windows TA 6.0 in order to get it working correctly with the current version of Security Essentials 2.3.1?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Let me research this -- my comment above did not age well.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Any update on this issue? Experiencing same issue with Windows TA 6.0 and SSE 2.4.2.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks David. I understand current situation.
The reason why I choose renderxml option, because windows event logs are recorded as multi byte character such as Japanese. So we choose renderxml option in common with Japan.
This is the sample windows security event in Japanese.
LogName=Security
SourceName=Microsoft Windows security auditing.
EventCode=4799
EventType=0
Type=情報
ComputerName=svrsplunk
TaskCategory=Security Group Management
OpCode=情報
RecordNumber=31817
Keywords=成功の監査
Message=セキュリティが有効なローカル グループ メンバーシップが列挙されました。