- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
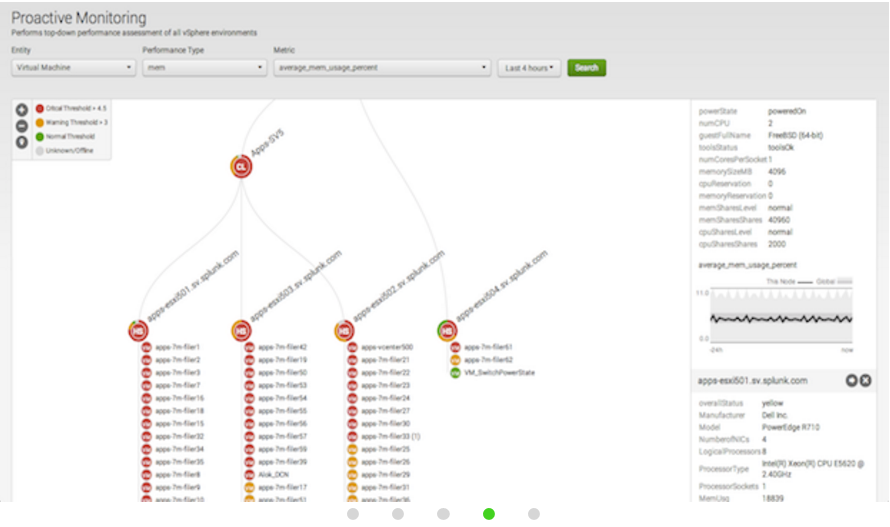
I am trying to implement the hierarchical tree mapping dashboard similar to the one in Proactive Monitoring dashboard of App : Splunk App for VMWare
Problem is I don't have any Vmware performance data to populate this graph, also unable to find any sample logs online. If possible, can anybody share the link where I can find this sample data. (I will use the sample to generate more events using EventGen)
Moreover I am trying to tweak the JavaScript file which includes searches, but the file is huge and will take time for me to understand. Although I am trying for it, it would be great if I can get some sample data or suggest some other way to implement the same.
Thanks in advance.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally able to load the dashboard.
I found the sample CSV's in "samples" folder of Splunk Add-On for Vmware (I regret not checking it first).
These CSV files includes the column for - index, source, host, sourcetype and raw ,which needs to be used while uploading.
At first, I uploaded a single file, only to see that the source column became "extracted_source" and host became "extracted_host" in interesting fields.
But I am able to resolve this using Field Alias setting, mentioning the "extracted_source" as source and "extracted_host" as host and raw as _raw for each sourcetype ,before CSV file upload.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Finally able to load the dashboard.
I found the sample CSV's in "samples" folder of Splunk Add-On for Vmware (I regret not checking it first).
These CSV files includes the column for - index, source, host, sourcetype and raw ,which needs to be used while uploading.
At first, I uploaded a single file, only to see that the source column became "extracted_source" and host became "extracted_host" in interesting fields.
But I am able to resolve this using Field Alias setting, mentioning the "extracted_source" as source and "extracted_host" as host and raw as _raw for each sourcetype ,before CSV file upload.