Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- How to send alert once if message doesn't change?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How to send alert once if message doesn't change?
Hi,
I am doing the sending alert if a machine has no activity in the span = 1h.
I configure to send it each hour. The thing is if the machine has no activity at 7:00, it will send the alert every hour (7h, 8h, 9h, etc) saying the same message that the machine has no activity at 7:00
Is anyway to send it once if the message is always the same (in this case, machine has no activity at 7:00).
If the machine is restarted, it has activities from 10:00 - 15:00, then it downs, I will receive an alert saying that machine has no activity at 15:00)
Thanks in advanced.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Julia1231,
did you tried to configure throttling for your alert?
You can do this in the alert definition page.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
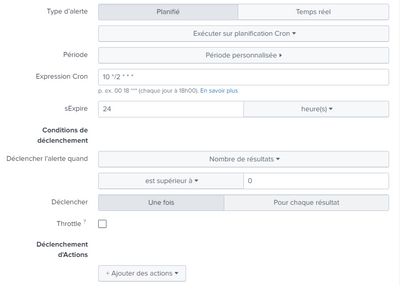
@gcusello This is my configuration:
Sorry it's in french but the function is same as in english. Do you find where I can do it please?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Julia1231,
you have to flag "Throttle" and define a time period that the alert will not be fired.
Only for the next time if you go in the address bar of your browser, replace "fr-FR" with "en-US", you'll have the dashboard in english, I'm italian and I usually have the same problem.
ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gcusello thank you.
So what I understand, because the Throttle goes with the Suppress triggering for (time), I can only suppress for the period that I define here.
For example if I put the suppress triggering for 3 hours, I will always receive the same email each 3h? It can reduce the number of duplicate email sent but cannot avoid, is it true?
And even if my machine is restarted, it has activity again, there is always the alert sent for inform a fault in the pass.
Thanks,
Julia
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @Julia1231,
my hint is to analyze throttle feature to use it at the best.
Otherwise a much more complicated workaround is to to write all your alerts in a summary index (as e.g. ES does) and then use this summary index to exclude the triggered alerts from results, but, as I said, it isn't so immediate to realize.
Ciao.
Giuseppe