- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, is there an alert action to save the results of the search directly to a specified, existing index?
I already tried the "Log event" alert action, but in the "Event" field that has to be specified, I did not know how to access the results of my search.
Thanks for your help!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Simon,
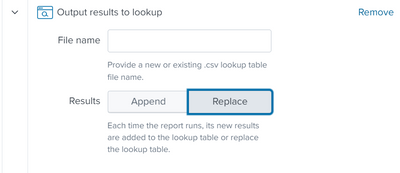
Thank you for providing additional context about your requirement. To make sure that you use the throttling part by saving the search as an alert, you can output the results of the search to a lookup using the alert action for sending data to a lookup and choosing the append or override results as per your convenience and then create another alert to use the data in the lookup and send it to an index using collect command as there is no alert action to send the data to an index by default in Splunk.
++If it helps, please consider accepting as an answer++
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There is a much easier solution for your requirement. You can use the collect command to route the data of your search to your desired index. You can even specify a sourcetype of your choice, but that will result into the data being counted against your license. By default, collect command uses sourcetype as stash. Please consider that while doing this.
your search
| collect index=<your_index>
More about the command: https://docs.splunk.com/Documentation/Splunk/latest/SearchReference/Collect
+++ Please consider accepting as an answer if this helps +++
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@shivanshu1593 Thanks for your answer.
The thing is that I don't want to do the data collection in my search as it would cause the "Throttle" option not to work.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Simon,
Thank you for providing additional context about your requirement. To make sure that you use the throttling part by saving the search as an alert, you can output the results of the search to a lookup using the alert action for sending data to a lookup and choosing the append or override results as per your convenience and then create another alert to use the data in the lookup and send it to an index using collect command as there is no alert action to send the data to an index by default in Splunk.
++If it helps, please consider accepting as an answer++
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Shiv,
thanks again for the answer.
I actually was aware of that solution, but don't find it very elegant or efficient. Facing that there is no better solution, I think I'll do it like you explained.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello Simon,
Since Splunk doesn't offer an alert action for exporting results to an index, unfortunately this is the only way via UI. You can always file this as an enhancement request for future versions of Splunk.
Best wishes,
Shiv
###If you found the answer helpful, kindly consider upvoting/accepting it as the answer as it helps other Splunkers find the solutions to similar issues###