- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
We have a search that will show both an Active Directory account that has been set to expire and it will also show if the account was moved to the correct Organizational Unit.
EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) | table _time, Account_Name, Account_Expires| append [|search EventCode=5139 [|search EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) |eval New_DN="CN=".replace(Account_Name,"\."," ").",OU=*,OU=Users - Disabled,DC=testdomain,DC=ca" | table New_DN] |table _time, Account_Name, New_DN, Old_DN]
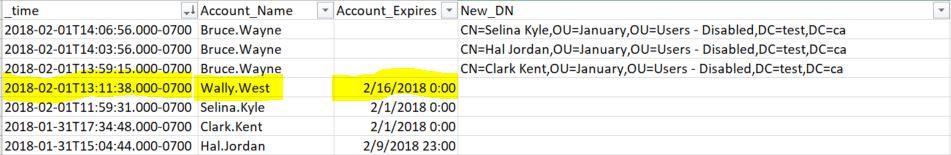
We would like to create an alert that would notify us if there is no match between the two with approximately 7 days. For example, as per the image below, an alert would notify us that "Wally.West" has not been moved to the Disabled OU within 7 days.
Any help with this would be greatly appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so we went back to the drawing board with this one and ended up changing how we search for the information. We have a task that collects the AD user data into a lookup table and am now able to show the SamAccountName, DistinguishedName, AccountExpires and has it set to show accounts that have reached over 10 days of the expires date :
| inputlookup ad-user-lookup | eval expires=strptime(AccountExpires,"%m/%d/%Y %H:%M:%S %p") | eval is_interesting=if(expires<now()-60*60*24*10,1,0) | search is_interesting=1 NOT DistinguishedName="*,OU=Users - Disabled,DC=testdomain,DC=ca" NOT DistinguishedName="*,OU=Training*" NOT DistinguishedName="*OU=Users - On Leave,DC=testdomain,DC=ca" | table SamAccountName, DistinguishedName, AccountExpires, expires, is_interesting
This will help us identify accounts that had an expire date set that are not in the On leave, Disabled or training OU's after 10 days.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok, so we went back to the drawing board with this one and ended up changing how we search for the information. We have a task that collects the AD user data into a lookup table and am now able to show the SamAccountName, DistinguishedName, AccountExpires and has it set to show accounts that have reached over 10 days of the expires date :
| inputlookup ad-user-lookup | eval expires=strptime(AccountExpires,"%m/%d/%Y %H:%M:%S %p") | eval is_interesting=if(expires<now()-60*60*24*10,1,0) | search is_interesting=1 NOT DistinguishedName="*,OU=Users - Disabled,DC=testdomain,DC=ca" NOT DistinguishedName="*,OU=Training*" NOT DistinguishedName="*OU=Users - On Leave,DC=testdomain,DC=ca" | table SamAccountName, DistinguishedName, AccountExpires, expires, is_interesting
This will help us identify accounts that had an expire date set that are not in the On leave, Disabled or training OU's after 10 days.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try (your alert should fire when below search result returns a results or number of events are greater than zero)
EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) | table _time, Account_Name, Account_Expires
| append [|search EventCode=5139 [|search EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) |eval New_DN="CN=".replace(Account_Name,"\."," ").",OU=*,OU=Users - Disabled,DC=testdomain,DC=ca" | eval TransferTime=_time | table TransferTime Account_Name New_DN]
|stats values(TransferTime) as TransferTime values(New_DN) as New_DN values(Account_Expires) as Account_Expired by Account_Name
| where isnull(TransferTime) OR abs(TransferTime-_time)>7*86400
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, thank you for the response!
I gave it a go and unfortunately it does not seem to be returning correct data. It had a mismatched "]", so I added it after "New_DN]]"
EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) | table _time, Account_Name, Account_Expires
| append [|search EventCode=5139 [|search EventCode=4738 Account_Expires!="-" | eval Account_Name=mvindex(Account_Name, -1) |eval New_DN="CN=".replace(Account_Name,"\."," ").",OU=*,OU=Users - Disabled,DC=testdomain,DC=ca" | eval TransferTime=_time | table TransferTime Account_Name New_DN]]
|stats values(TransferTime) as TransferTime values(New_DN) as New_DN values(Account_Expires) as Account_Expired by Account_Name
| where isnull(TransferTime) OR abs(TransferTime-_time)>7*86400
I am wondering if it is because the original search converts the account name from "bruce.wayne" to "bruce wayne" (period to a space).