Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Other Using Splunk
- :
- Alerting
- :
- Re: Alert when user is log off
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I need to get an alert when a user is log off from a server, here is my query
index="wineventlog" user="*.COM" OR user="*"
| head 1 | eval age = now() - _time
|table _time user name
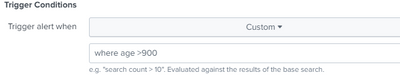
Then I'm setting a custom alert to
but I don't get any alert
Thank you,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ajromero I don't find age field in your table command, there could be other reasons.
- age > 900 condition might not met, you can try same query in UI with | where age > 900 at the end exactly select time similar to schedule window. Lower age threshold and retry.
- Your role/user assigned to these alerts to run alerts might not be having schedule search capability. You can run following query to find out what exactly happening with your search
index=_internal sourcetype="scheduler" savedsearch_name=<your_search_name>
- While configuring alert in UI ,Trigger Action under Alerts should be selected to Email and provide the correct email
- could be issues while sending email to SMTP server , you can verify here.
index=_internal source="/opt/splunk/var/log/splunk/python.log" subject="<your_email_subject>" sendemail ERROR
----------
An upvote would be appreciated if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ajromero
Can you try this works? added age field to table command.
index="wineventlog" user="*.COM" OR user="*"
| head 1 | eval age = now() - _time
|table _time user name age----
An upvote would be appreciated if it helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I already have the age field in the table and it doesn't do it
index="wineventlog" user="*.COM" OR user="*"
| head 1 | eval age = now() - _time
|table _time user name
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @ajromero I don't find age field in your table command, there could be other reasons.
- age > 900 condition might not met, you can try same query in UI with | where age > 900 at the end exactly select time similar to schedule window. Lower age threshold and retry.
- Your role/user assigned to these alerts to run alerts might not be having schedule search capability. You can run following query to find out what exactly happening with your search
index=_internal sourcetype="scheduler" savedsearch_name=<your_search_name>
- While configuring alert in UI ,Trigger Action under Alerts should be selected to Email and provide the correct email
- could be issues while sending email to SMTP server , you can verify here.
index=_internal source="/opt/splunk/var/log/splunk/python.log" subject="<your_email_subject>" sendemail ERROR
----------
An upvote would be appreciated if it helps!