Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- How can I hide rows with duplicate values in an xy...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
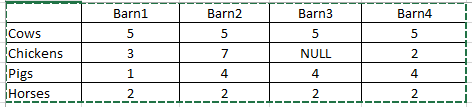
I have a large table generated by xyseries where most rows have data values that are identical (across the row). I want to hide the rows that have identical values and only show rows where one or more of the values are different or contain the fillnull value (NULL). Consider this xyseries table:
In this example, the Cows and Horses rows would be hidden because they contain identical data values. Only the Chickens and Pigs rows should be displayed because they have mismatched data values. I have tried dedup but it does not work against the xyseries and it will not catch the missing events where the value is fillnull'ed.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this
your current search just before the xyseries command, say with field animal, barn, count
| eventstats dc(count) as uniqValues by animal | where uniqValues>1
| xyseries animal barn count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try something like this
your current search just before the xyseries command, say with field animal, barn, count
| eventstats dc(count) as uniqValues by animal | where uniqValues>1
| xyseries animal barn count
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No workie 😞
The tail end of my search now looks like this:
| eventstats dc(count) as uniqValues by Object | where uniqValues>1 | xyseries Object computer Version | fillnull value="Missing"
I get no events found when I run this. If I pull out the eventstats and where statements, I get results with duplicates. The object field is made from some strings that are smashed together to give a complete file path. Just for giggles, I created a field called OMD from the md5 sum of the Object field and tweaked your idea accordingly:
| eval OMD=md5(Object) | eventstats dc(count) as uniqValues by OMD | where uniqValues>1 | xyseries Object computer Version | fillnull value="Missing"
Still no results.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
your current search WITH xyseries and fillnull command
| untable Object computer Version
| eventstats dc(Version) as uniqValues by Object | where uniqValues>1
| xyseries Object computer Version | fillnull value="Missing"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked! You rock!