Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- What is the time format for epoch time with .00000...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What is the time format for epoch time with .000000 ?
Hi,
I have build a report to extract several fields.
Summary Indexing by default send result into the "stash" sourcetype. This is how splunk knows that data is already in splunk and my summary data will not be account for additional license.
But I want to change the time parameter in stash sourcetype.
I have a field "timestamp" in my log in epoch time : I would like to index my logs with the "timestamp" field, but it does not work.
I create a props.conf in my app :
[stash]
TIME_PREFIX = timestamp\=\"
TIME_FORMAT = %s
I also tried TIMESTAMP_FIELDS = timestamp but no more result.
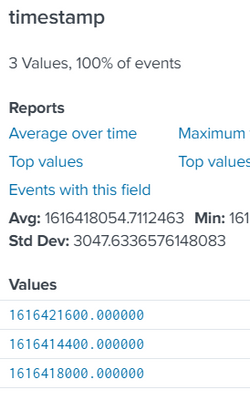
Example of timestamp value :
How can I give timestamp value in _time field ? Can you help me please ?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@mah While Creating summary index add below eval condition to get timestamp value from timestamp fieldname-
...|eval _time=timestamp
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @493669 ,
The problem is when I want to filter the time picker to "last 60 minutes", show me nothing because splunk indexes in UTC.
Example value :
_time = 3/22/21 3:10:00.000 PM
timestamp = 1616425200.000000
Even if I add :
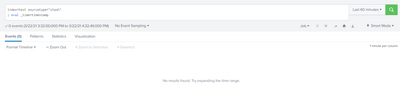
index=test sourcetype=stash |eval _time=timestampwith time picker filter to "last 60 minutes", I get nothing :
whereas when I increase time picker to "last 4 hour", I have events on last hour :
How can I deal with that ?