Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- How does the Universal Forwarder Detects the Sourc...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How does the Universal Forwarder Detects the Source field in a WIndows Event Log?
I'm collecting the System logs from a Windows 2012 R2 DHCP Server using Splunk Universal forwarder 9.0.1.0 to a Splunk Enterprise 8.2.5 indexer. Initially I was collecting all logs using this stanza
[WinEventLog://System]
start_from = oldest
disabled = 0
current_only = 0
As per the inputs.conf guide here it states that for the allowed key values in an WindowsEvent log monitoring stanza we may use
| SourceName | The source of the entity that generated the event. Corresponds to Source in Event Viewer. |
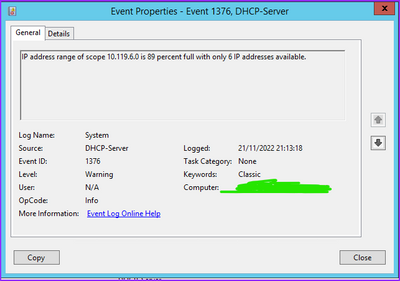
I wished to reduce the number of events collected to only those related to DHCP. When I look into the windows event viewer I see this event for example
However, if I search for any event in my indexed data from this server with
SoureName = DHCP-Server
there are no results. A simple query over all time like this shows this
index=windowsdhcp
| stats count by SourceName
Howver, in the putput of the stats of all Sourcenames I see this Sourcename namely Microsoft-Windows-DHCP-Server. So I got back to windows event vierwer and look at the XML view of the event which is as follows:
- <Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
- <System>
<Provider Name="Microsoft-Windows-DHCP-Server" Guid="{6D64F02C-A125-4DAC-9A01-F0555B41CA84}" EventSourceName="DhcpServer" />
<EventID Qualifiers="0">1376</EventID>
<Version>0</Version>
<Level>3</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2022-11-21T17:14:28.000000000Z" />
<EventRecordID>1236733</EventRecordID>
<Correlation />
<Execution ProcessID="0" ThreadID="0" />
<Channel>System</Channel>
<Computer>vmsys305.vhihealthcare.net</Computer>
<Security />
</System>
- <EventData>
<Data>10.119.6.0</Data>
<Data>89</Data>
<Data>6</Data>
</EventData>
</Event>
There is no mention of the event with Source=Microsoft-Windows-DHCP-Server. The Providername is the same however. I then press the Copy button which yeilds the following pasted data (to notepad):
Log Name: System
Source: Microsoft-Windows-DHCP-Server
Date: 21/11/2022 21:13:18
Event ID: 1376
Task Category: None
Level: Warning
Keywords: Classic
User: N/A
Computer: vmsys609.vhihealthcare.net
Description:
IP address range of scope 10.119.6.0 is 89 percent full with only 6 IP addresses available.
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-DHCP-Server" Guid="{6D64F02C-A125-4DAC-9A01-F0555B41CA84}" EventSourceName="DhcpServer" />
<EventID Qualifiers="0">1376</EventID>
<Version>0</Version>
<Level>3</Level>
<Task>0</Task>
<Opcode>0</Opcode>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2022-11-21T21:13:18.000000000Z" />
<EventRecordID>93904</EventRecordID>
<Correlation />
<Execution ProcessID="0" ThreadID="0" />
<Channel>System</Channel>
<Computer>vmsys609.vhihealthcare.net</Computer>
<Security />
</System>
<EventData>
<Data>10.119.6.0</Data>
<Data>89</Data>
<Data>6</Data>
</EventData>
</Event>
So now we have our SourceName=Source mapping.
Summary
So this leads me to belive that the sttaement from this guide regarding the SourceName being equivelent to the Source as seen in Windows event viewer requires some clarifcaiton namely that it is as viewed from the output of the copy of the xml view of the event not the default output.