Are you a member of the Splunk Community?
- Find Answers
- :
- Splunk Platform
- :
- Splunk Enterprise
- :
- Help displaying another table panel which displays...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hello
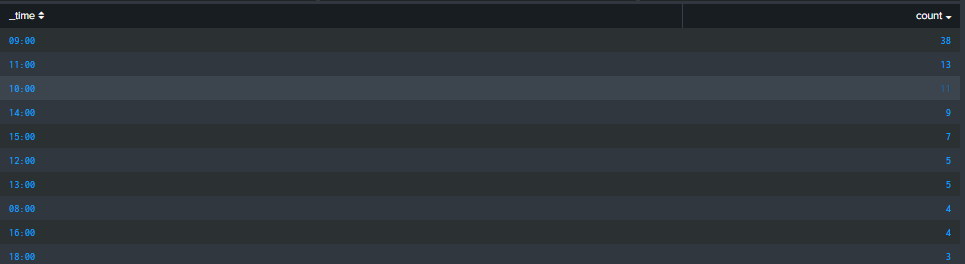
As you can see, I stats events by _time in a first table panel
When I click on the result count I need to display an other table panel which displays the results of the value clicked
What is wrong in my example?
thanks
<panel>
<table>
<search>
<query>index=toto sourcetype=tutu
| stats count as count by _time</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">cell</option>
<option name="refresh.display">progressbar</option>
<drilldown>
<set token="count">$click.value$</set>
</drilldown>
</table>
</panel>
<panel depends="$count$">
<table>
<search>
<query>index=toto sourcetype=tutu
| search count=$count$
| table _time crash_process_name count</query>
<earliest>$field1.earliest$</earliest>
<latest>$field1.latest$</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tokens are just named temporary storage areas, they do not have to be related to the field they came from or being compared to.
<set token"tom">**bleep**</set>
| where harry=$tom$where tom is the name of the token, **bleep** is just a string value, and harry is a field in the events
So, yes, you could set a token to contain a value of _time, but you cannot set it to be the current value of _time in the event you are using it in.
I hope that makes sense, and does not confuse you further.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Is count a field in the events returned by
index=toto sourcetype=tutu
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
hi what do you mean exactly?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| search count=$count$
is looking for a field called count with the value from the $count$ token
If this field doesn't exist, you are unlikely to get any results!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes in my first table I have a value for count field
so when I click on it I dont understnd why there is nothing even if I use
| search count=$count$
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What are you expecting the search in the second panel to find?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Do you know if it is possible to use _time as a token?
If yes why my example doesnt works instead the example with "name" field works?
thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Tokens are just named temporary storage areas, they do not have to be related to the field they came from or being compared to.
<set token"tom">**bleep**</set>
| where harry=$tom$where tom is the name of the token, **bleep** is just a string value, and harry is a field in the events
So, yes, you could set a token to contain a value of _time, but you cannot set it to be the current value of _time in the event you are using it in.
I hope that makes sense, and does not confuse you further.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
what is strange is that I am doing a similar thing with the field "name" it works!
<row>
<panel>
<table>
<search>
<query>index=toto sourcetype=tutu
| stats count(crash_process_name) as crash by name</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">cell</option>
<option name="refresh.display">progressbar</option>
<drilldown>
<set token="name">$click.value$</set>
</drilldown>
</table>
</panel>
<panel depends="$name$">
<table>
<search>
<query>index=toto sourcetype=tutu
| search name="$name$"
| stats last(crash_process_name) as crash count as count by name</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>but if I am doing the same with the field _time, it doesnt works!
<row>
<panel>
<table>
<search>
<query>index=toto sourcetype=tutu
| stats count(crash_process_name) as crash by _time</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">cell</option>
<option name="refresh.display">progressbar</option>
<drilldown>
<set token="name">$click.value$</set>
</drilldown>
</table>
</panel>
<panel depends="$_time$">
<table>
<search>
<query>index=toto sourcetype=tutu
| search _time="$_time$"
| stats last(crash_process_name) as crash count as count by _time</query>
<earliest>-24h@h</earliest>
<latest>now</latest>
</search>
<option name="drilldown">none</option>
<option name="refresh.display">progressbar</option>
</table>
</panel>
</row>- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
when I click on the count onf my first table panel, I need to display all the events there is in this count
For example when _time is 09:00 I need to display the details of the 38 events there is in my count