Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- use inputlookup with field index and count as sub ...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
use inputlookup with field index and count as sub search
bapun18
Communicator
09-04-2019
05:55 AM
I have an inputlookup which have 2 fields index and count, I need to create an alert so that alert will trigger when we have greater value of real index values mentioned over count field in lookup.
I have used following query but I want to get pass the index name as a sub search to inputlookup.
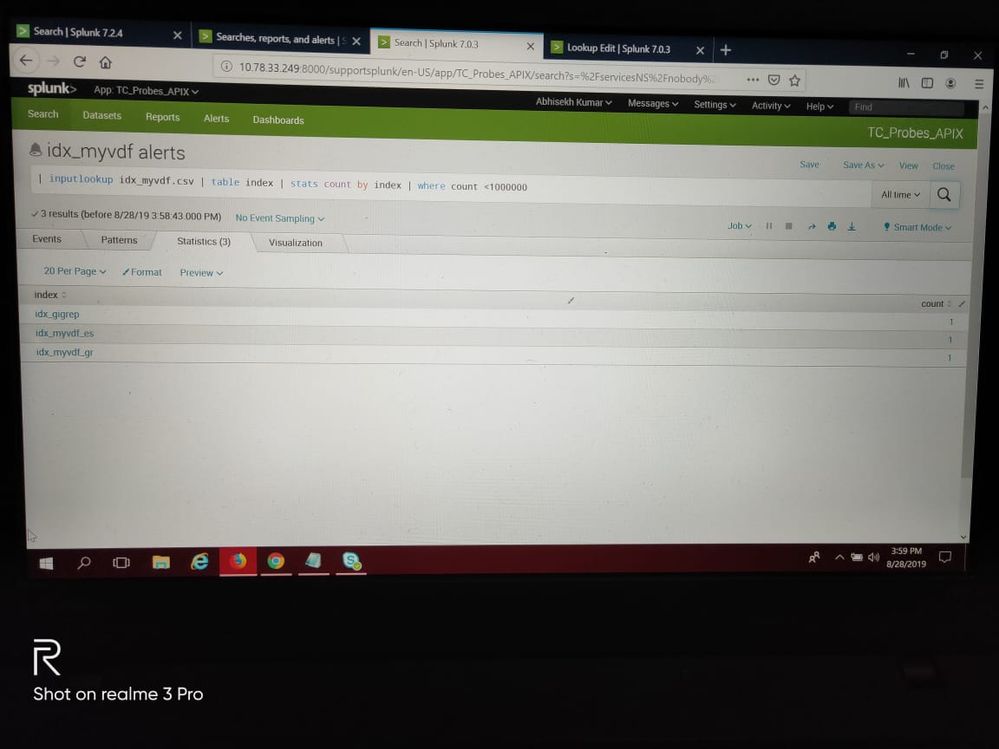
|inputlookup idx_myvdf.csv | table index | stats count by index | where count > 0
I have tried below query as well, but still no result, want to pass index name mentioned under lookup and their actual count and then I want to put where count > actual_count
|tstats c by index where index[|inputlookup idx_myvdf.csv | rename index AS actual_index | fields actual_index] | table indexcount actual_index actual_count
Please suggest it's urgent
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
09-04-2019
09:04 AM
@bapun18,
Try
| tstats count where (index=* OR index=_*) by index
| lookup idx_myvdf.csv index OUTPUT count as threshold
| appendcols [|inputlookup idx_myvdf.csv|where index="default"|fields count|rename count as default|filldown default
| eval threshold=coalesce(threshold,default)|where count > threshold
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
Get Updates on the Splunk Community!
Index This | What is broken 80% of the time by February?
December 2025 Edition
Hayyy Splunk Education Enthusiasts and the Eternally Curious!
We’re back with this ...
Unlock Faster Time-to-Value on Edge and Ingest Processor with New SPL2 Pipeline ...
Hello Splunk Community,
We're thrilled to share an exciting update that will help you manage your data more ...
Splunk MCP & Agentic AI: Machine Data Without Limits
Discover how the Splunk Model Context Protocol (MCP) Server can revolutionize the way your organization uses ...