Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- search time data masking
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
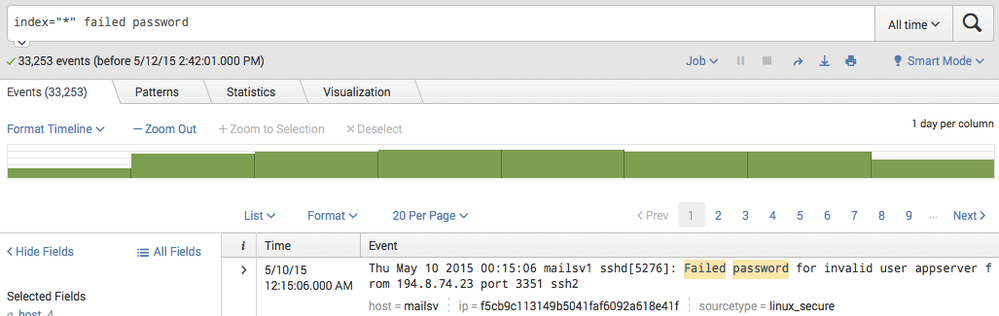
Hi
I am trying to mask indexed data using following props.conf comfig for linux_secure.
[linux_secure]
EXTRACT-ip = (?<ip>\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})
EVAL-ip = md5(ip)
EVAL-_raw = replace(_raw,"(\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})",ip)
I try to mask IP address and replace the IP address with hashed value(mp5), but replacement portion does not work with the config above. Still ip address in raw event is not hashed.
The desired _raw and ip field look like this:
Does anyone know how to configure props.conf to replace ip raw data into hashed ip data?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You cant overwrite _raw at search time with EXTRACT or REPORT. Only through spl in the eval method you're using.
http://answers.splunk.com/answers/3025/search-time-mask.html
http://answers.splunk.com/answers/26137/how-can-i-mask-data-both-at-index-time-and-search-time.html
Other options would be either a macro, or mask this at index time with SEDCMD.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You cant overwrite _raw at search time with EXTRACT or REPORT. Only through spl in the eval method you're using.
http://answers.splunk.com/answers/3025/search-time-mask.html
http://answers.splunk.com/answers/26137/how-can-i-mask-data-both-at-index-time-and-search-time.html
Other options would be either a macro, or mask this at index time with SEDCMD.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
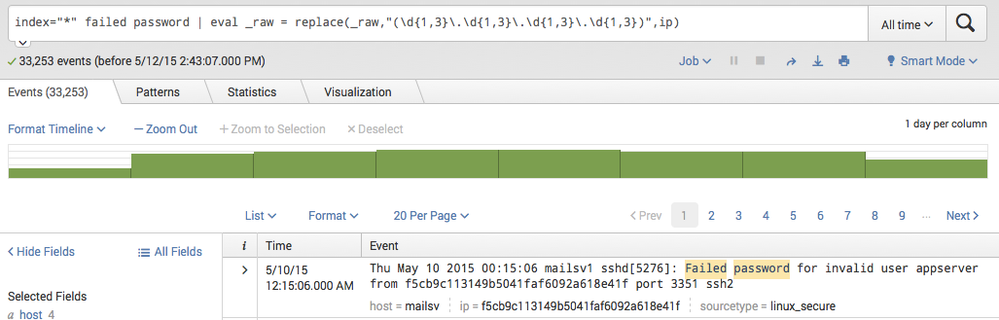
esix, thank you for your commend.
After several trials and errors, I ended up with the config below.
This works for me.
[linux_secure]
EXTRACT-ip1 = (?<ip>\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3})
EVAL-_raw = replace(_raw,"(\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3})",md5(ip))
EVAL-ip = md5(ip)
I am looking for the way to hide ip by using _ip as a field name.
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This worked great for us as well, thank you for sharing.