Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- rex field extraction
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
rex field extraction
I am getting familiar with splunk commands, trying to extract hostname from an extracted field called monitor_name. monitor_name field data look like this,
[Linux][FWA Electronic Channel Messaging][l91oma1][Process][SS][/fiwlspoma4/was/INSTANCE1/profiles/base/servers/server1][error]
[Linux][Baseline][vlrtp569][Process][OSWatcher][SiSExclude]
[Linux][Baseline][vlrtp123][Process][srmclient][SiSExclude]
I would like to extract l91oma1, vlrtp569,vlrtp123 from the above field using rex command. Can someone help me with the regular expression.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi anoopambli
This search code work well
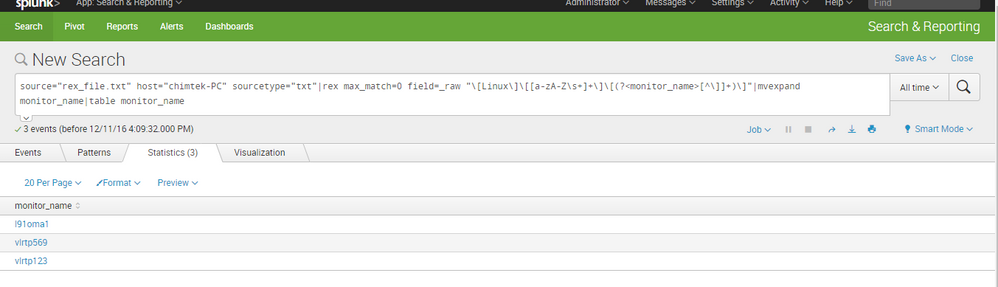
...................................|rex max_match=0 field=_raw "\[Linux\]\[[a-zA-Z\s+]+\]\[(?<monitor_name>[^\]]+)\]"|mvexpand monitor_name|table monitor_name
Look at my result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
use this
rex field=_raw "^(?:[^\[\n]*\[){3}(?P<fieldname>\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@kml_uvce your escaping backslashes were lost since you forgot to use the "code" tags around your regex. The regex should actually look like below:
rex field=_raw "^(?:[^\[\n]*[){3}(?P<fieldname>w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And there is backslash missing before "w+" as well. So it should be
rex field=_raw "^(?:[^\[\n]*[){3}(?P<fieldname>\w+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks everyone, that helped me.