- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
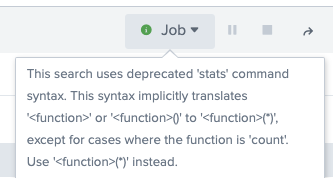
- "This search uses deprecated 'stats' command synta...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting this informational message when running "stats count" commands:
This search uses deprecated 'stats' command syntax. This syntax implicitly translates '<function>' or '<function>()' to '<function>(*)', except for cases where the function is 'count'. Use '<function>(*)' instead.I don't understand it. What am I doing wrong and what should I be doing instead? A sample of the stats command generating the message above:
| stats sparkline count(Destination) AS sessions by Destination_URL, Destination_userIDThanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Turns out it's a bug - the "deprecated syntax" notification is not supposed to happen - thanks @mattness for the post!
"Turns out this particular example is a bug. Splunk 8.0.0 through 8.0.6 generates this "info message" when you use sparkline without an argument (such as sparkline(count) or sparkline(count(cpu)). This isn't supposed to happen. The bug is fixed in upcoming versions of Splunk."
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The sparkline argument should be a function, perhaps
| stats sparkline(count(Destination)) AS sessions by Destination_URL, Destination_userIDIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That removes the session count field though. This one:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So add it back in.
| stats sparkline(count(Destination)), count(Destination)) AS sessions by Destination_URL, Destination_userIDIf this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I did. 🙂 But doesn't that means "stats" is then run twice for the same dataset, thus unnecessarily increasing the "cost" of the search? (And somewhat clogging it, making it just a teeny bit less readable?)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@richgalloway just in case you have the bandwidth for a follow up question...
Here is the sample search in "Add sparklines to search results" Splunk KB article for 8.0.5 (latest) release:
index=_internal | chart sparkline count by sourcetype
It produces the same dreaded "deprecated syntax" notification in my 8.04.1 instance.
Questions:
- How would you modify this search to remove the notification yet retain both the sparkline and the "count" field?
- Would it make sense to try asking a new question, something like "what are Splunk recommendations on using non-deprecated 'stats' command syntax that is as performant as the deprecated one?"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How do you know which syntax is more performant? Does the Job Inspector show a noticeable difference?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> That command works without error on my 8.0.4 instance.
This gives me the green "deprecated syntax" informational message in 8.04.1, 8.05:
index=_internal
| chart sparkline count by sourcetype> How do you know which syntax is more performant? Does the Job Inspector show a noticeable difference?
About 10-20% faster for the "deprecated" one vs. the one you came up with, with two "count" functions.
| stats sparkline(count(Destination)), count(Destination))
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Turns out it's a bug - the "deprecated syntax" notification is not supposed to happen - thanks @mattness for the post!
"Turns out this particular example is a bug. Splunk 8.0.0 through 8.0.6 generates this "info message" when you use sparkline without an argument (such as sparkline(count) or sparkline(count(cpu)). This isn't supposed to happen. The bug is fixed in upcoming versions of Splunk."
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oh, and submit feedback on the docs page that uses that syntax so they can correct it.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
index=_internal | chart sparkline count by sourcetype
https://docs.splunk.com/Documentation/Splunk/8.0.5/Search/Addsparklinestosearchresults
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Typo on my part (grabbed the wrong SPL from the docs). Corrected. The solution you're proposing is the one with the problem and the one I have questions about.