Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: measuring overall success rate based off two t...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
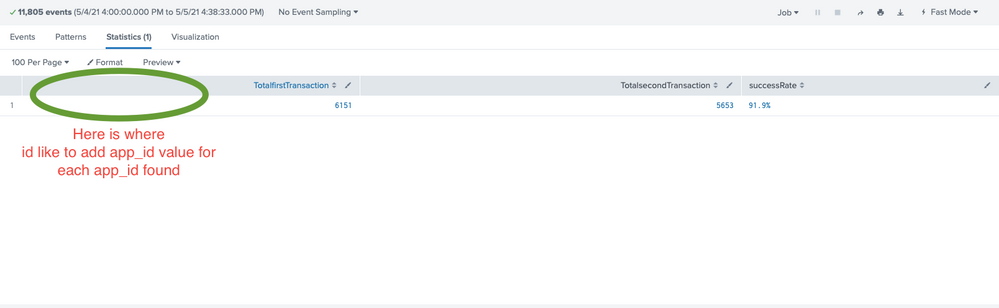
I am trying to measure our success rate on our platform. there are two individual events which we care to see in order to consider a transaction 'successful'. The two event_names we are looking for are "TRANSACTIONA" and "TRANSACTIONB" . The tricky part here is that i don't only want to know the overall success rate, but i want each individual success rate to be grouped by a field which i am creating in my query using rex. the field here is 'app_id'.
I already have the overall success rate working in the below query, but trying to get these same 3 stats grouped for each individual app_id found is where i am having issues. Below is my current working query, looking to be extended into groups for each app_id:
index=jj3 "TRANSACTIONA" OR "TRANSACTIONB" | rex field=log "\"app_id\": \W(?<app_id>\w+)\W" | rex field=log "\"event_name\": \W(?<event_name>[a-zA-Z-|_|:]+)\W" | eval firstTransaction=if(event_name=="TRANSACTIONA", 1, 0) | eval secondTransaction=if(event_name=="TRANSACTIONB", 1, 0) | stats sum(firstTransaction) as TotalfirstTransaction sum(secondTransaction) as TotalsecondTransaction | eval successRate=round(TotalsecondTransaction/TotalfirstTransaction*100, 1)."%"
So essentially i want:
for each app_id found, i want to stats the following into output :
App_id, TotalfirstTransaction, TotalsecondTransaction, successRate
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| stats sum(firstTransaction) as TotalfirstTransaction sum(secondTransaction) as TotalsecondTransaction by app_id | fields app_id TotalfirstTransaction TotalsecondTransaction | eval -----------
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| stats sum(firstTransaction) as TotalfirstTransaction sum(secondTransaction) as TotalsecondTransaction by app_id | fields app_id TotalfirstTransaction TotalsecondTransaction | eval -----------
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@sravankaripe wondering if you can help me refine this same query you provided me to show me the same data, but just represented in a week over week comparison. is that possible using my current query?
something like:
App_id, TotalfirstTransaction, TotalsecondTransaction, successRate, currentWeeksuccessRate, PreviousWeek, 3Weeks ago
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
my query as of right now is:
index=jj3 "TRANSACTIONA" OR "TRANSACTIONB" | rex field=log "\"app_id\": \W(?<app_id>\w+)\W" | rex field=log "\"event_name\": \W(?<event_name>[a-zA-Z-|_|:]+)\W" | eval firstTransaction=if(event_name=="TRANSACTIONA", 1, 0) | eval secondTransaction=if(event_name=="TRANSACTIONB", 1, 0) | stats sum(firstTransaction) as TotalfirstTransaction sum(secondTransaction) as TotalsecondTransaction by app_id | dedup app_id | eval successRate=round(TotalsecondTransaction/TotalfirstTransaction*100, 1)."%" | fillnull successRate | sort - successRate | search NOT successRate=0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thank you! looks like i was very close after all. this is what i wanted.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Could you please some example how your events look like and what is your expected output
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
because my log events contain sensitive data, i cannot share that. but i can provide you the expected output of what I'm looking to generate, extending what i have currently.