Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- join/append two queries
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
join/append two queries
Hi,
I have two different queries, I want to join two columns.
Below is my query:
`macro`
msg="Finish import*" OR msg = "*inserted for*"
| rex field=msg "Finish import (?<dataField>.+)\s*at\s+(?P<datetime>\S+\s+\S+) processing time=(?<processingTime>\w+)" | where trim(dataField)="postcode"
| append [
search `macro` msg="*inserted for*"
| rex field=msg "(?<records>\d+)+\s[^\s].+for(?<dataField1>.*)" | where trim(dataField1)="postcode" ]
| eval records1 = records+":"+processingTime
| transaction msg maxpause=100s |
strcat records "::" processingTime recordsPr |
table datetime, dataField, records,ts,processingTime, recordsPr,dataField1.
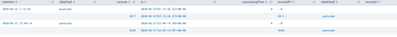
I want to combine records and processingTime in one column like records:processingTime.
With eval records1 its doesnot concatenate but with string concatenate it looks like below:
Any help, would be appreciated.
Thanks,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since append creates a new record combining fields using eval won't work. Try using join command instead of append.
Then eval should work