- Splunk Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- how to label the attributing events additional fie...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here are the screenshots:
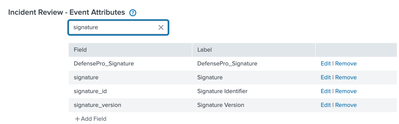
In incident review setting, I have already labeled signature:
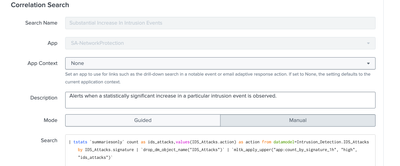
Then in Correlation Search content setting, also I have setting the search query which could result in fields with signature. This search can be run normally in search head and show the result I want.
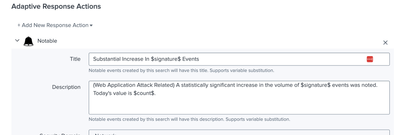
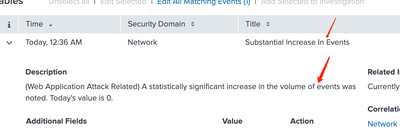
But here related to drill-down search or description, this $signature$ can not show in notable of incident review:
May I ask how to solve this issue?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jaro,
to see a field in the fields of a Notable (in the Incident Review dashboard) you have to check if this field is displayed in the Notable event (running index=notable search=your_correlation_search),
if not, probably isn't displayed in the output of the correlation search: manually run your correlation search and see if the field is displayed, if not add it to the correlation Search.
One additional hint: don't modify the Correlation Search, but clone it and modify and enable only the cloned one.
If the field is present in the Notable event, you have also to check if it's present in the default visible fields, that you can find these configurations at [Configure > Incident management > Incident Review Settings] in the section Incident Review - Event Attributes.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jaro,
to see a field in the fields of a Notable (in the Incident Review dashboard) you have to check if this field is displayed in the Notable event (running index=notable search=your_correlation_search),
if not, probably isn't displayed in the output of the correlation search: manually run your correlation search and see if the field is displayed, if not add it to the correlation Search.
One additional hint: don't modify the Correlation Search, but clone it and modify and enable only the cloned one.
If the field is present in the Notable event, you have also to check if it's present in the default visible fields, that you can find these configurations at [Configure > Incident management > Incident Review Settings] in the section Incident Review - Event Attributes.
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @gcusello. ---to check if this field is displayed in the Notable event (running index=notable search=your_correlation_search), yes, I have display the result "signature" in the search I ran. However, the below description can not show the field value "signature" I search in correlation search as $signature$.
Also I have tried eval other name equal to field signature, still nothing.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jaro ,
if the field is in the Notable index, can be displayed.
Did you checked if it's in the visualized fields?
Ciao.
Giuseppe
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
It's OKAY now. In next triggered notable, it displayed. Thank you @gcusello.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @jaro ,
good for you, see next time!
Ciao and happy splunking
Giuseppe
P.S.: Karma Points are appreciated 😉