Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- merge succesrate query with timechart
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how should I merge this 2 query into 1:
query 1)
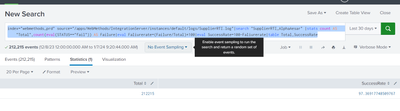
index="XXXX" source="XXXX"|search "SupplierRTI_AlphaAesar" |stats count AS "Total",count(eval(STATUS=="fail")) AS Failure|eval Faliurerate=(Failure/Total)*100|eval SuccessRate=100-Faliurerate|table Total,SuccessRate
query 2)
index="webmethods_prd" source="/apps/WebMethods/IntegrationServer/instances/default/logs/SupplierRTI.log"|search "SupplierRTI_AlphaAesar" | timechart span=1w count
I want a report like this
how should I form the query?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
index="webmethods_prd" source="/apps/WebMethods/IntegrationServer/instances/default/logs/SupplierRTI.log" "SupplierRTI_AlphaAesar"
| timechart span=1w
count(eval('STATUS'=="fail")) as Failure,
count as Total
| eval
Failurerate=('Failure'/'Total')*100,
SuccessRate=100-'Failurerate'
| fields + _time, Total, SuccessRate
Just by looking at your original queries I think the above SPL will do what you are asking for.
Though, your text of query1 shows the index as XXXXXX but the screenshot show the same index/source as query2 so I was a little confused by that part.
Let me know if you actually need to data from 2 different index/source together in a final report and I can give it another shot.
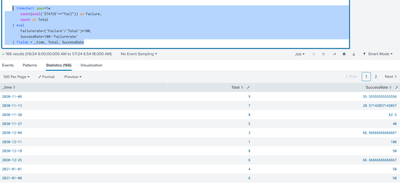
Example of output from simulated data:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Give this a try
index="webmethods_prd" source="/apps/WebMethods/IntegrationServer/instances/default/logs/SupplierRTI.log" "SupplierRTI_AlphaAesar"
| timechart span=1w
count(eval('STATUS'=="fail")) as Failure,
count as Total
| eval
Failurerate=('Failure'/'Total')*100,
SuccessRate=100-'Failurerate'
| fields + _time, Total, SuccessRate
Just by looking at your original queries I think the above SPL will do what you are asking for.
Though, your text of query1 shows the index as XXXXXX but the screenshot show the same index/source as query2 so I was a little confused by that part.
Let me know if you actually need to data from 2 different index/source together in a final report and I can give it another shot.
Example of output from simulated data: