Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- how to keep sender name with space in search resul...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am using Splunk Enterprise Version: 9.1.0.1.
my search query is :
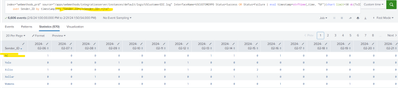
index="webmethods_prd" source="/apps/webmethods/integrationserver/instances/default/logs/USCustomerEDI.log" InterfaceName=USCUSTOMERPO Status=Success OR Status=Failure | eval timestamp=strftime(_time, "%F")|chart limit=30 dc(TxID) over Sender_ID by timestamp
in result I am getting incomplete Sender_ID, splunk removed space from Sender_ID
but actually it should be full name , like this :
How can I preserve the full Sender_ID here?
Avik
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have not shown how Sender_ID has been extracted. Having said that, you may need to re-extract it with a rex command, such as this:
| rex "Sender_ID=(?<Sender_ID>.+)\s Receiver_ID"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
used rex "Receiver_ID =(?<Receiver_ID>.+)\s TxnType" and worked
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
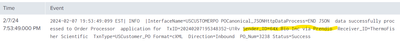
Sender_ID is present in log line:
2024-02-16 09:55:41:829 EST| INFO |InterfaceName=USCUSTOMERPO POCanonical_JSONHttpDataProcess=END JSON data successfully processed to Order Processor application for TxID=20240216095535623-0EEu Sender_ID=hC Bioscience Inc Receiver_ID=ThermoFisher Scientific TxnType=USCustomer_PO Format=cXML Direction=Inbound PO_Num=2550 Status=Success
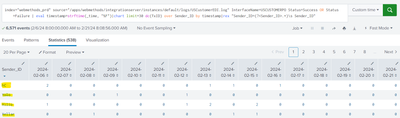
I have updated the query bit still space is truncated
InterfaceName=USCUSTOMERPO Status=Success OR Status=Failure | eval timestamp=strftime(_time, "%F")|chart limit=30 dc(TxID) over Sender_ID by timestamp|rex "Sender_ID=(?<Sender_ID>.+)\s"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You have not shown how Sender_ID has been extracted. Having said that, you may need to re-extract it with a rex command, such as this:
| rex "Sender_ID=(?<Sender_ID>.+)\s Receiver_ID"- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please help to extract Receiver_ID also, how should I regex it?
Receiver_ID ='Thermo Fisher Sci West Palm Beach' TxnType=
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sender_ID is present in logging:
as example:
2024-02-16 09:55:41:829 EST| INFO |InterfaceName=USCUSTOMERPO POCanonical_JSONHttpDataProcess=END JSON data successfully processed to Order Processor application for TxID=20240216095535623-0EEu Sender_ID=hC Bioscience Inc Receiver_ID=ThermoFisher Scientific TxnType=USCustomer_PO Format=cXML Direction=Inbound PO_Num=2550 Status=Success
please help to form the query :
i tried this but still the issue persist
it is taking only 1st word from log line