Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: how can i do to make this events into Splunk?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
how can i do to make this events into Splunk?
hello team!
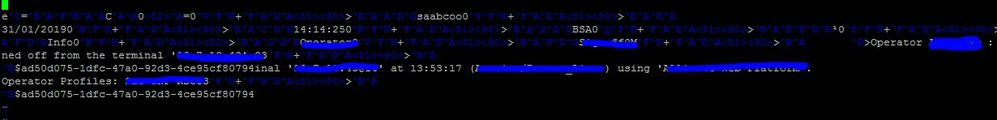
We have this logs comming in a port 10162 (say that this is a kind of "syslog" but it comes with a lot of special characters :
I have been trying a lot of sourcetypes and sometimes the splunk took a little portion of the log, for example:
So finally I make a custom sourcetype but now the splunk dont process any event. The configuration of the sourcetype is:
binary_check is false
truncate is in 0
Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
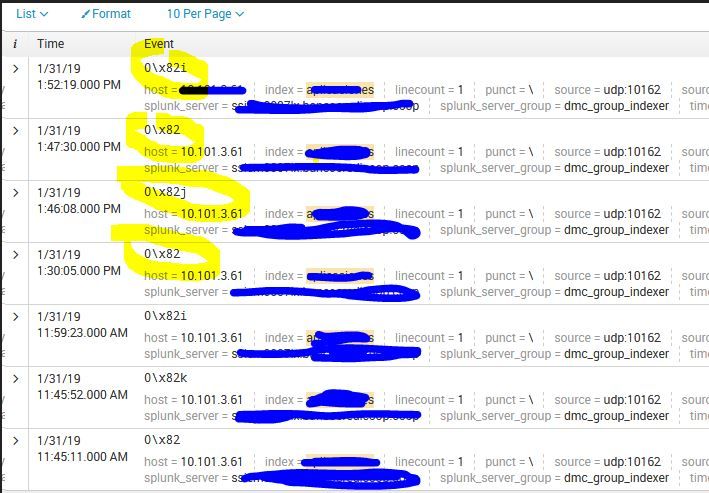
The values with \x are garbage values coming into splunk which is making logs looks unformated .
usage of sed command in props will remove those garbage value and make logs look formatted .
Please include below in your props and test it
[sourcetype]
SEDCMD-null = s/\x82//g
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @lightech1
Someone else might have a better answer than me, but I would make sure this parsing props is set - which should fix the wierd line breaking
SHOULD_LINEMERGE = false
As you have said, NO_BINARY_CHECK = false should be also set on the place where data is ingested.
All the best