Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- field value is being extracted as fieldname in reg...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
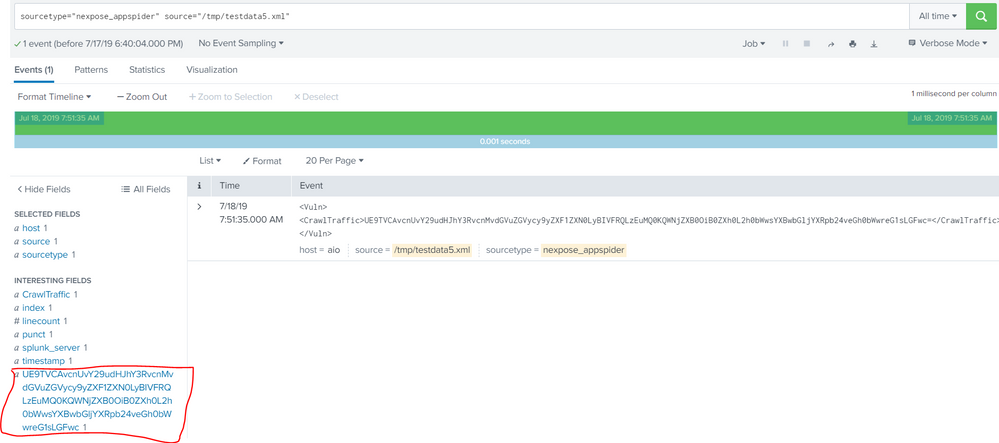
I am trying to extract xml fields using regex but I am encourtering this issue for this specific tags, It is working with other tags. I have tested my regex in regex101 and it is working properly. https://regex101.com/r/ivJjTE/1
In this example below, CrawlTraffic is being extracted properly, but CrawlTraffic value is also being extracted as a new field with "" as a value.
props.conf
[nexpose_appspider]
TRANSFORMS-null= setnull
BREAK_ONLY_BEFORE = <Vuln>
NO_BINARY_CHECK = true
TIME_FORMAT = %Y-%m-%d %H:%M:%S
TIME_PREFIX = <ScanDate>
MAX_TIMESTAMP_LOOKAHEAD = 19
TRUNCATE = 0
disabled = false
pulldown_type = true
REPORT-xmlext11 = xml-extr11
transforms.conf
[xml-extr11]
REGEX = <([^>]+)>([^<]*)<\/\1>
FORMAT = $1::$2
MV_ADD = true
REPEAT_MATCH = true
[setnull]
REGEX = <VulnSummary>
DEST_KEY = queue
FORMAT = nullQueue
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
you should add KV_MODE=none in props.conf for nexpose_appspider sourcetype.
By default KV_MODE is set to auto.
It will ensure that splunk will not try to extract key=value pattern.
In your exemple the value of CrawlTraffic finishes by "=".
Splunk extracts the pattern. That's why the value is empty.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello,
you should add KV_MODE=none in props.conf for nexpose_appspider sourcetype.
By default KV_MODE is set to auto.
It will ensure that splunk will not try to extract key=value pattern.
In your exemple the value of CrawlTraffic finishes by "=".
Splunk extracts the pattern. That's why the value is empty.