Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: eval if to post on part of a string
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a question on the use of eval on a UA String. I want to do a lookup on a UA String and call out the version of Chrome the UA String has. At the moment I have covered most UA Strings however I would to display only a part of the UA String to table that into a count stats.
Current UA String =
Mozilla/5.0+(Windows+NT+6.3;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/80.0.3987.149+Safari/537.36
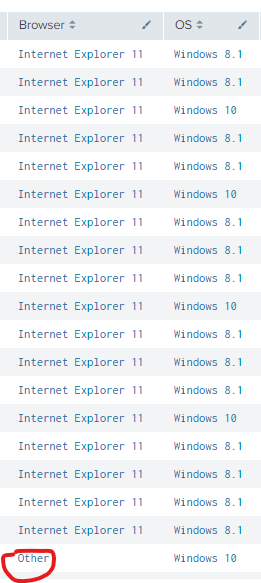
At the moment I just have everything other then IE to list as other, however, I'd like to list that as the Chrome Browser Version.
This is my current search:
| eval Browser=case(like(cs_User_Agent,"%;+MSIE+8.0;%"), "Internet Explorer 8", like(cs_User_Agent,"%+MSIE+ 7.0%"), "Internet Explorer 8", like(cs_User_Agent,"%;+MSIE+9.0;%"), "Internet Explorer 9", like(cs_User_Agent,"%;+MSIE+10.0;%"), "Internet Explorer 10", like(cs_User_Agent,"%;+rv:11.0%"), "Internet Explorer 11", like(cs_User_Agent,"%;+Trident/7.0;+%"), "Internet Explorer 11", 1==1, "Other")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One approach you could take is to do it like this
| rex field=cs_User_Agent "(?<BrowserInfo>(\+rv|Trident|MSIE|Chrome).[^\+;]*)"
| rex field=BrowserInfo "[:\/ ](?<Version>.*)"
| eval Browser=case(match(BrowserInfo, "^Trident|MSIE|rv"), "Internet Explorer", match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| eval Browser=if(!isnull(Version),Browser." ".Version, Browser)Rather than having a long expensive case/like statement, it attempts to get the browser family to the BrowserInfo field and then to get the version from there.
It may not do exactly what you are after, there are hundreds of UA strings around, but it might give you a different path to solving the problem.
Hope this helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One approach you could take is to do it like this
| rex field=cs_User_Agent "(?<BrowserInfo>(\+rv|Trident|MSIE|Chrome).[^\+;]*)"
| rex field=BrowserInfo "[:\/ ](?<Version>.*)"
| eval Browser=case(match(BrowserInfo, "^Trident|MSIE|rv"), "Internet Explorer", match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| eval Browser=if(!isnull(Version),Browser." ".Version, Browser)Rather than having a long expensive case/like statement, it attempts to get the browser family to the BrowserInfo field and then to get the version from there.
It may not do exactly what you are after, there are hundreds of UA strings around, but it might give you a different path to solving the problem.
Hope this helps
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi, this is great for Chrome but now it's all wrong with Internet Explorer. The results I get are not correct. Most of these are IE11 and yet I am now getting IE7. The Trident version is 7.0 but IE11 moved away from MSIE versions since IE11 and now its on the Trident platform.
I think I need to drill down on what you're syntax is as I am not famliar with rex.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I suspected, it wouldn't be the perfect hammer 🙂
The rex statement uses regular expressions to extract fields from your data, so my example showed a simple pattern based on some UA header examples, but as there are so many, it may be challenging to get a good pattern.
When playing with regular expressions, you can use this site to test your patterns.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok thanks, would it be reasonable to combine mine with yours. As I have Internet Explorer down its just the Chrome field I need and that is consistent.
Issue when I tried is that one overwrites the other so "Other" replaces all IE or vica versa all Chrome replaces "Other" if you get my idea?
This is what I had just to capture Chrome:
| rex field=cs_User_Agent "(?<BrowserInfo>(\Chrome).[^\+;]*)"
| rex field=BrowserInfo "[:\/ ](?<Version>.*)"
| eval Browser=case(match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| eval Browser=if(!isnull(Version),Browser." ".Version, Browser)
| table LHD, cs_username, a_app, cs_User_Agent, Browser, BrowserInfo, Version, a_request, _time | dedup cs_username sortby +LHD
this look ok
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have already set Browser with your existing case statement, then when assigning a new value for the Chrome, you can avoid it overwriting Browser like this
| eval Browser=case(!isnull(Browser), Browser, match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")So the first case statement will check if Browser is already set and go no further with other cases.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great that worked however, now I have to create two new fields. Is there a way to append the results into all BrowserInfo?
this is the code:
| rex field=cs_User_Agent "(?<BrowserInfo>(\Chrome).[^\+;]*)"
| rex field=BrowserInfo "[:\/ ](?<Version>.*)"
| eval Browser=case(match(BrowserInfo, "^Chrome"), "Chrome")
| eval Browser=if(!isnull(Version),Browser." ".Version, Browser)
| eval Browser=case(like(cs_User_Agent,"%;+MSIE+8.0;%"), "Internet Explorer 8", like(cs_User_Agent,"%+MSIE+ 7.0%"), "Internet Explorer 8", like(cs_User_Agent,"%;+MSIE+9.0;%"), "Internet Explorer 9", like(cs_User_Agent,"%;+MSIE+10.0;%"), "Internet Explorer 10", like(cs_User_Agent,"%;+rv:11.0%"), "Internet Explorer 11", like(cs_User_Agent,"%;+Trident/7.0;+%"), "Internet Explorer 11", 1==1, "Other") | eval OS=case(like(cs_User_Agent,"%Windows+NT+5.1%"), "Windows XP", like(cs_User_Agent,"%Windows+NT+ 6.0;%"), "Windows Vista", like(cs_User_Agent,"%Windows+NT+6.1;%"), "Windows 7", like(cs_User_Agent,"%Windows+NT+6.2%"), "Windows 8", like(cs_User_Agent,"%Windows+NT+6.3;%"), "Windows 8.1", like(cs_User_Agent,"%Windows+NT+10.0;%"), "Windows 10", 1==1, "Other") | eval Browser=case(!isnull(Browser), Browser, match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| eval BrowserInfo=coalesce(BrowserInfo, Browser)- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Legend, this worked great. Just one concern I have. The addition of this line, below, is only looking for Chrome, If Internet Explorer was in the Browser field it would list it as "Other"?
| eval Browser=case(!isnull(Browser), Browser, match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| rex field=cs_User_Agent "(?<BrowserInfo>(\Chrome).[^\+;]*)"
| rex field=BrowserInfo "[:\/ ](?<Version>.*)"
| eval Browser=case(match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| eval Browser=if(!isnull(Version),Browser." ".Version, Browser)
| eval Browser=case(like(cs_User_Agent,"%;+MSIE+8.0;%"), "Internet Explorer 8", like(cs_User_Agent,"%+MSIE+ 7.0%"), "Internet Explorer 8", like(cs_User_Agent,"%;+MSIE+9.0;%"), "Internet Explorer 9", like(cs_User_Agent,"%;+MSIE+10.0;%"), "Internet Explorer 10", like(cs_User_Agent,"%;+rv:11.0%"), "Internet Explorer 11", like(cs_User_Agent,"%;+Trident/7.0;+%"), "Internet Explorer 11", like(cs_User_Agent,"%+Chrome%"), "Chrome", 1==1, "Other")
| eval OS=case(like(cs_User_Agent,"%Windows+NT+5.1%"), "Windows XP", like(cs_User_Agent,"%Windows+NT+ 6.0;%"), "Windows Vista", like(cs_User_Agent,"%Windows+NT+6.1;%"), "Windows 7", like(cs_User_Agent,"%Windows+NT+6.2%"), "Windows 8", like(cs_User_Agent,"%Windows+NT+6.3;%"), "Windows 8.1", like(cs_User_Agent,"%Windows+NT+10.0;%"), "Windows 10", 1==1, "Other")
| eval Browser=case(!isnull(Browser), Browser, match(BrowserInfo, "^Chrome"), "Chrome", 1==1,"Other")
| eval BrowserInfo=coalesce(BrowserInfo, Browser, Version)
| table LHD, cs_username, a_app, OS, BrowserInfo, _time, cs_User_Agent
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, the first case statement
!isnull(Browser), Browseris saying that if the Browser field is currently NOT NULL, then use the existing value of Browser field, so if it is already set to Internet Explorer, it will use that value. Only if the Browser field is null then it will go on to the match/other clauses of the case statement.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Ok so it all good then?
Big thanks buddy
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I could not find what I wanted in this:
https://docs.splunk.com/Documentation/Splunk/8.0.5/SearchReference/TextFunctions