Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: count eval results doesn't match the results u...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a simple search with stats count eval (u_id is a numeric field):
index=myindex base search | stats count(eval(u_id=1234)) as total
The count which I see under "total" (under Statistics tab) does not match the number under Events tab.It seems the eval function is not performing right. But when I do the following search both number matches.
index=myindex base search u_id=1234| stats count as total
what's wrong with the first search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I would guess it's because in your first search, the count in the Events tab is showing all of the events returned by the base search. You're then using a transforming command (stats) to produce your result.
In the second search, you're filtering the events as part of that search (using the u_id=1234). So the count in the Events tab will be reduced.
For example if I do this:
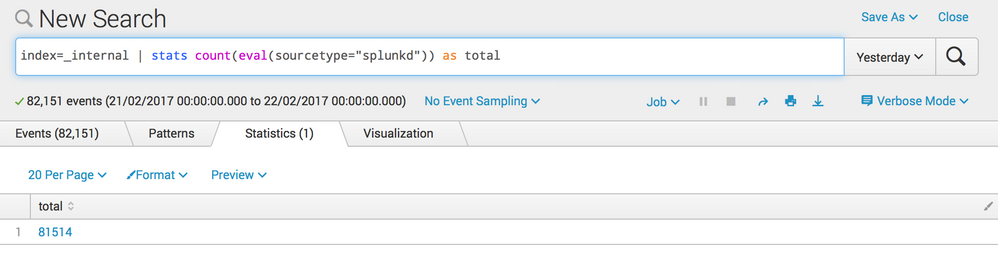
index=_internal | stats count(eval(sourcetype="splunkd")) as total
I'll get:
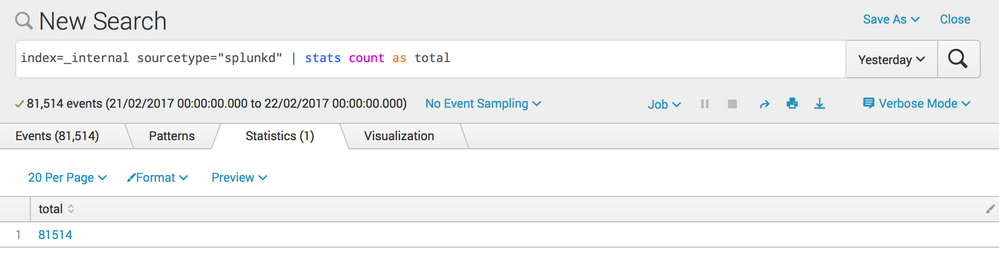
But if I do this:
index=_internal sourcetype="splunkd" | stats count as total
I get:
Whilst it's not 'strictly' true, you could think of the count in the Events tab as showing you the number of events your actual search returned, before applying any sort of transformation. Such as stats, chart, etc.
Does that make sense?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I would guess it's because in your first search, the count in the Events tab is showing all of the events returned by the base search. You're then using a transforming command (stats) to produce your result.
In the second search, you're filtering the events as part of that search (using the u_id=1234). So the count in the Events tab will be reduced.
For example if I do this:
index=_internal | stats count(eval(sourcetype="splunkd")) as total
I'll get:
But if I do this:
index=_internal sourcetype="splunkd" | stats count as total
I get:
Whilst it's not 'strictly' true, you could think of the count in the Events tab as showing you the number of events your actual search returned, before applying any sort of transformation. Such as stats, chart, etc.
Does that make sense?