Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- appending statistics to same table cell
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have a search that is a series of multikv fields for Linux. this is leveraging the sourcetype=interfaces in the default Unix app.
I am attempting to attach a 'total throughput' field to the back of each NIC in parenthesis. I've seen this done before, but I can't remember how to do this, so any help would be appreciated. I am using stats values() as it keeps everything very neat, and keeping this clean is my goal.
This is my search currently:
index=myIndex sourcetype=interfaces | eval total=(RXbytes + TXbytes)/1024/1024/1024 | eval errors=(TXerrors + RXerrors) | where total>0 | stats values(Name) as NIC sum(total) as total by host
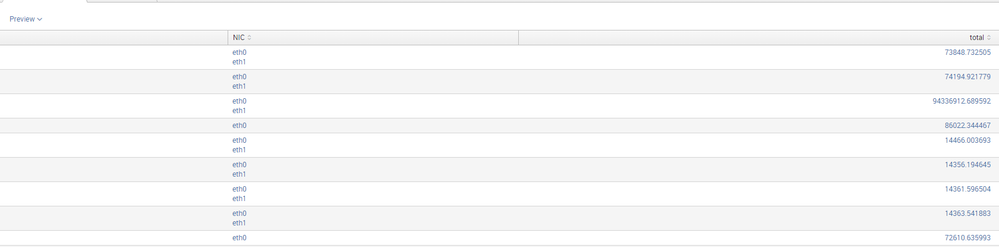
This gives me a result that looks like this:
You'll notice that there is only a single 'sum' on each host, and i'm looking to append the 'total' field, per NIC, per host in parenthesis to the NIC.
If that's not possible, then a single total per NIC per host would be great as well, but not using the 'table' command, or something generic. That's too messy with hundreds of hosts, and up to 10 NIC's a piece, so I'm looking for something cleaner.
Any suggestions are appreciated, Thank you!!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just decided to build my own field for this, and add the relevant information.
This is my final search:
index=myIndexsourcetype=interfaces
| eval total=(RXbytes + TXbytes)/1024/1024/1024
| eval error=(TXerrors + RXerrors)
| where total>0
| bucket _time span=5m
| stats latest(total) as GB latest(error) as errors by Name hostname
| eval total=round(GB,2)
| eval combine=("NIC: " + Name." --- ". GB +" GB"." --- ". errors + " errors")
| stats values(combine) as totalsByNIC by hostname
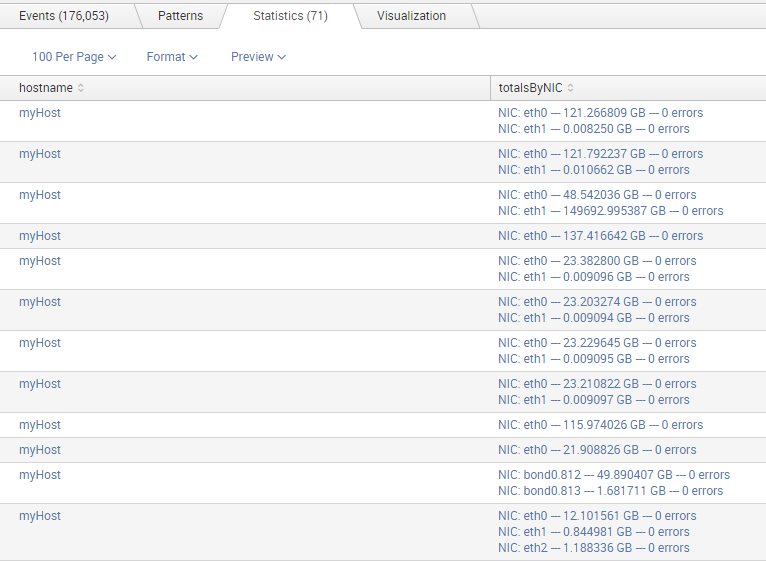
And this is the final visualization:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just decided to build my own field for this, and add the relevant information.
This is my final search:
index=myIndexsourcetype=interfaces
| eval total=(RXbytes + TXbytes)/1024/1024/1024
| eval error=(TXerrors + RXerrors)
| where total>0
| bucket _time span=5m
| stats latest(total) as GB latest(error) as errors by Name hostname
| eval total=round(GB,2)
| eval combine=("NIC: " + Name." --- ". GB +" GB"." --- ". errors + " errors")
| stats values(combine) as totalsByNIC by hostname
And this is the final visualization:
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Perhaps ... | stats sum(total) as total by host,Name ?
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Negatory my friend. This gets me a sum within a table. Thank you though!