- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Why am I unable to properly join data from two ind...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why am I unable to properly join data from two indexes?
Hi All,
I am trying to link 2 indexes using join.
I have tried the following code:
index=index1| join Id[index=index2]
In this case, only one instance of the records are being joined and the same instance is overwritten across the records.
I have also tried the following code:
index=index1| join type=inner Id[index=index2]
In this case, some of all the records are being matched. However, all the records are not being matched.
It will be really great if someone could help me understand the issue and propose some solution.. 😄
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Dilip.
As @aljohnson mentioned this flowchart will help you http://docs.splunk.com/Documentation/Splunk/6.3.3/Search/Abouteventcorrelation
You do not need join in your case as all the events you have contain the Id field. What you want instead is something like:
index=index1 OR index=index2 | stats values(*) AS * by Id
I strongly recommend learning the stats command - have a good read through http://docs.splunk.com/Documentation/Splunk/6.3.3/SearchReference/Stats
Also be sure to run through the search tutorial if you have not already done so: http://docs.splunk.com/Documentation/Splunk/6.3.3/SearchTutorial/WelcometotheSearchTutorial
If your coming from a database background it might help to think of your Splunk data as a single table - as such there is rarely a need to use join
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you give some more details on what you are actually trying to do? For example, after the join, are you hoping to get some timecharts, visualizations, or statistics from the data? If so, there is a very good chance that you do not need to use join.
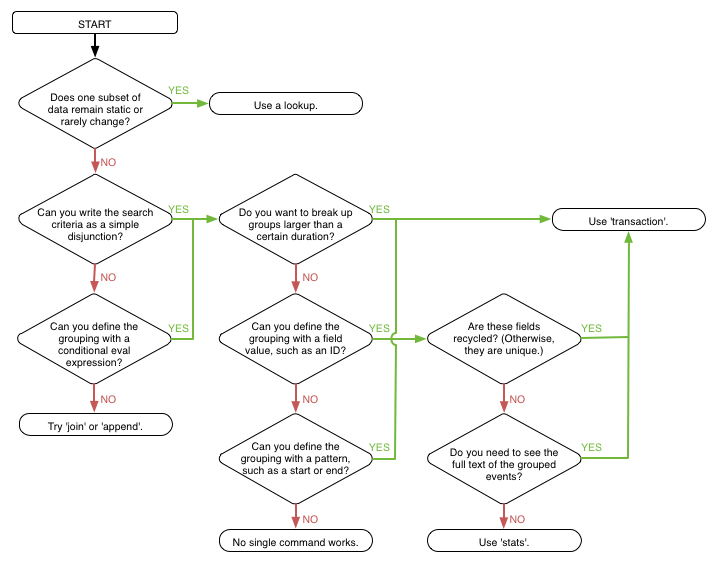
from here.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi alialjohnson,
Thanks for your response. I am doing a join because the I need to extract some of the information present in Index2 and join it with information in Index1.
The final objective is to represent it either as a table or visualization trend.
Also, is it possible to utilize append query to join 2 indexes based on the values of a common field
Thanks again for your help.. 🙂
Regards,
Dilip
