Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Why am I getting an error when doing field ext...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'm trying to extract a field with the field extractor tool, however, keep getting errors back
This is a part of the sample log event containing the fields:
<pfId>208431</pfId><isoId>208431</isoId>
both these fields tend to have the same values most of the time, and I'm trying to root out instances where they don't have the same values. So tried to display them with the query
| table pfId, isoId
but it doesn't work - shows up as empty tables
Appreciate any help I can get with this.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something in the spirit of \<pfId\>(.*?)\<\/pfId\> should work.
Please use - Regular expressions 101
A good thread - Splunking HTML Formatted Log Files
Please test with -
index=<any index>
| eval _raw="<pfId>208431</pfId><isoId>208431</isoId>"
| rex field=_raw "\<pfId\>(?<pfId>.*?)\<\/pfId\>"
| rex field=_raw "\<isoId\>(?<isoId>.*?)\<\/isoId\>"
It should produce the pfId and isoId fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tried this
index=WPG
| eval _raw="<pfId>208431</pfId><isoId>208431</isoId>"
| rex field=_raw "\<pfId\>(?<pfId>.*?)\<\/pfId\>"
| rex field=_raw "\<isoId\>(?<isoId>.*?)\<\/isoId\>" | table pfId, isoId | transpose |
and it works !
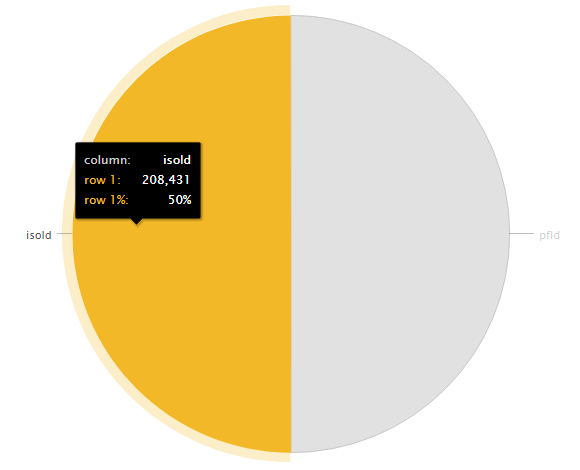
given that there was only two main IDs used for both pfID and isoID I've gone with a pie chart.
Thanks everyone for your help really appreciate it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want help resolving your issues with the field extractor, it would help if you would explain your attempts and the errors you got.
A simple rex command solution to extract these two fields in your query could look like this:
| rex "pfId\>(?<pfId>[^\>]+)"
| rex "isoId\>(?<isoId>[^\>]+)"
Alternatively, you could have a look at the xmlkv command: http://docs.splunk.com/Documentation/Splunk/7.0.1/SearchReference/Xmlkv
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks ! tried it.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something in the spirit of \<pfId\>(.*?)\<\/pfId\> should work.
Please use - Regular expressions 101
A good thread - Splunking HTML Formatted Log Files
Please test with -
index=<any index>
| eval _raw="<pfId>208431</pfId><isoId>208431</isoId>"
| rex field=_raw "\<pfId\>(?<pfId>.*?)\<\/pfId\>"
| rex field=_raw "\<isoId\>(?<isoId>.*?)\<\/isoId\>"
It should produce the pfId and isoId fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
tried it and it works thanks !
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tanp685 - great to hear - btw, it's customary to drop on us some good points if we are helpful ; -)
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've converted this comment to an Answer. @tanp685 - You can up-vote this answer, and still accept your own answer for your question, or accept this answer if you would like to do that.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
... | rex "\<pfId\>(?<pfId>\d+?)\<" | | rex "\<isoId\>(?<isoId>\d+?)\<" | search pfId=isoId | table pfId, isoId
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
thanks! it works
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Are the fields extracted? You state that you keep getting errors with the Field Extraction Tool, so I'm assuming that you aren't getting the fields when you try to do the table command because if the fields are empty, you will get no data from the table command.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
no they weren't. but the rex commands worked.