- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi All,
I have a search string like below:
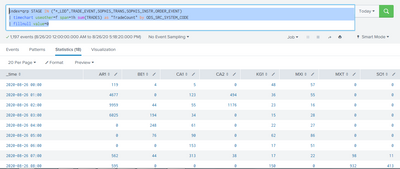
index=qrp STAGE IN ("*_LDD",TRADE_EVENT,SOPHIS_TRANS,SOPHIS_INSTR,ORDER_EVENT)
| timechart useother=f span=1h sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE
| fillnull value=0
And the result screenshot is below. The AR1, BE1 ect are source system codes and the numerical values for each source system in the rows are the aggregate trade counts for respective source system at that time span starting from 00:00:00 hours.
I want to schedule an alert at 8 a.m in the morning which should get triggered when the whole summation of the trade aggregates values from 00:00:00 hours till 08:00:00 hours for each source system is not more that threshold 2000.
For example, in the above screenshot, we can see the summation of trades for source system MXT is 1030 between 00:00:00 till 08:00:00 hours which is below threshold and alert email notification should be sent.
Could you please help with how to set up my search string and what should be my alert triggering condition?
Thanks in advance. Your help is much appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Timechart probably is not the best choice for an alert since you likely don't care about values over time so much as the most recent value. Try stats, instead.
index=qrp STAGE IN ("*_LDD",TRADE_EVENT,SOPHIS_TRANS,SOPHIS_INSTR,ORDER_EVENT)
| bin span=1h
| stats sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE
| where TradeCount < 2000
You may omit the bin command if the alert is scheduled to run at 8am and has a time window of 8 hours.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Something like set your span to 8h and then trigger the alert on custom condition of "search TradeCount < 2000"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Timechart probably is not the best choice for an alert since you likely don't care about values over time so much as the most recent value. Try stats, instead.
index=qrp STAGE IN ("*_LDD",TRADE_EVENT,SOPHIS_TRANS,SOPHIS_INSTR,ORDER_EVENT)
| bin span=1h
| stats sum(TRADES) as "TradeCount" by ODS_SRC_SYSTEM_CODE
| where TradeCount < 2000
You may omit the bin command if the alert is scheduled to run at 8am and has a time window of 8 hours.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @richgalloway Thank you so much for your detailed explanation with the search string. I was in need of this solution only for my business requirement.
Many thanks. 🙂