Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Variable reference in To: field of an email alert.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Variable reference in To: field of an email alert.
Hi Splunk Team.
Can I use variable reference in To: field of an email alert? I have a distribution_list variable associated with my sourcetype and it is set to correct email address depending on date and time.
U put $result.distribution_list$ in the To: field, but it does not send email.
Thanks
Michal
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @mdzmuran
Yes you can use $result.distribution_list$ format in TO: field, however the search results should be having the value populated to distribution_list field, did you verify it?
How are you so sure email not been sent just checking the inbox ? Sometimes the Splunk user has been restricted to schedule alerts. Can you run following query to find out errors associated to your alert?
index=_internal source=*scheduler.log ERROR OR WARN
To find send email errors,
index=_internal source=*python.log sendemail ERROR OR WARN
Hope mail server already configured in Splunk.
---
An upvote would be appreciated and Accept solution if this reply helps!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HIi venkatasri.
The alerts are triggered, I can see them in Triggered alerts.
If I replace $result.distribution_list$ with regular email address, the emails are sent.
The queries suggested do not return any data. It may be due to access permissions, I asked administrators to run them.
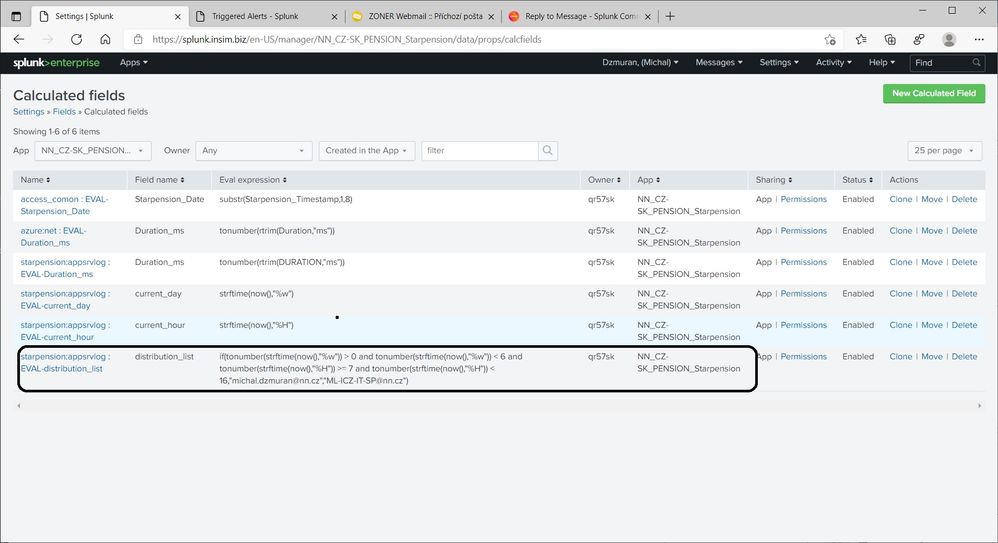
One more info, it may be important. The distribution_list variable is not defined in the search query. It is defined in the Calculated Fields setting for this particular sourcetype. I can see it, however, in the search results if I run the alert query manually.
Michal
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As per docs the field shall be explicitly available in results. Try including distribution_list to results using | fields command. Hope this helps!
| $result.fieldname$ | First value for the specified field name from the first search result row. Verify that the search generates the field being accessed. |