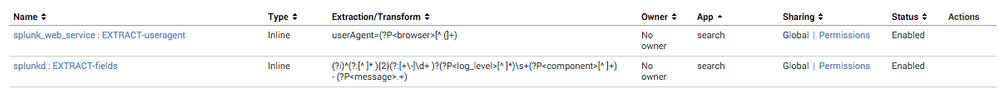Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Using my custom app with only one sourcetype inclu...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am in the middle of the development of the XXXX Splunk App, which is built on top the TA XXXX I built before. Obviously I have a sourcetype in this app called XXXX-CEF, thus that all the XXXX events parsed with this sourcetype are parsed the right way. This means I can only see the fields of my sourcetype in the search of my XXXX Splunk App.
After finishing building searches just for my XXXX events, I started creating searches also including events parsed by a different sourcetype using still the search of my XXXX Splunk App. For some reason my XXXX Splunk App only has the fields of my XXXX sourcetype, and if I want to search a different index with events parsed with a different sourcetype, I can’t search for the fields of this different sourcetype in my app. Only the official Splunk “Search and Reporting App” works for that. Is this right? Is there any way to make my XXXX App include all the fields of all the sourcetype used by the Splunk instance?
Thanks for the help,
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you plan on publishing the app or distributing it you need to either package the props/transforms that are needed to make these fields or include a requirement that they install the other TAs that include the extractions. The only way to make the extractions work within your XXXX Splunk App on your search head is to find the extractions and change the permissions to "global" instead of "local". If the extraction is "local" to the "Search and Reporting App" then you won't be able to see it in your XXXX Splunk App. Take a look at the image below, these two extractions are saved in the "search" app, but are also global so other apps can use them.
Hope this helps,
GTRI Splunk Team!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you plan on publishing the app or distributing it you need to either package the props/transforms that are needed to make these fields or include a requirement that they install the other TAs that include the extractions. The only way to make the extractions work within your XXXX Splunk App on your search head is to find the extractions and change the permissions to "global" instead of "local". If the extraction is "local" to the "Search and Reporting App" then you won't be able to see it in your XXXX Splunk App. Take a look at the image below, these two extractions are saved in the "search" app, but are also global so other apps can use them.
Hope this helps,
GTRI Splunk Team!