Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Use EVAL and Case for Windows EventCodes to provid...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Using this code I am able to generate a table for IIS Application Pool specific errors. With the eval-case providing a little info about the EventCode.
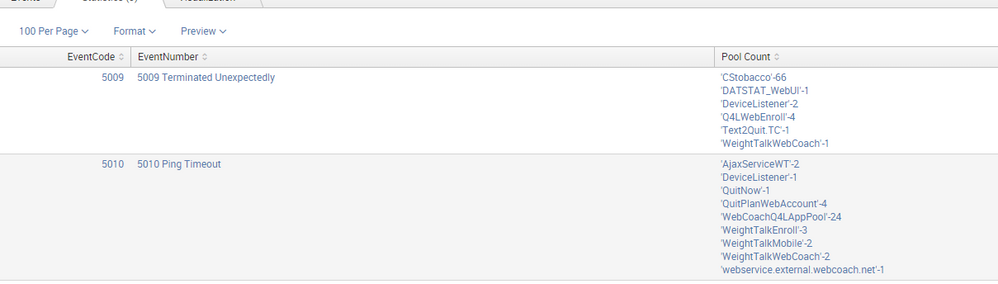
(host=stwweb0* NOT host=stwweb0*I) sourcetype=WinEventLog:System SourceName="Microsoft-Windows-WAS" NOT 5186 | rex field=Message "(?i) pool (?P<Pool>[^ ]+)" |eval EventNumber=case(EventCode=5009 ,"5009 Terminated Unexpectedly",EventCode=5011,"5011 Communication Error",EventCode=5012,"5012 exceeded time limits during start up",EventCode=5013,"5013, exceeded time limits during shut down" ,EventCode=5014,"5014, internal error in its process management",EventCode=5074,"5074, worker process reached its allowed processing time limit",EventCode=5079,"5079, An administrator has requested a recycle",EventCode=5076,"5076, scheduled recycle time",EventCode=5138,"5138, failed to stop a listener channel for protocol 'http' in the allotted time",EventCode=5080,"5080, Recycled due to system settings change",EventCode=5010,"5010 Ping Timeout") |stats count by EventCode Pool EventNumber|eval Pool=Pool."-".count | stats list(Pool) as "Pool Count" by EventCode EventNumber
This returns a happy little list.
The problem is if there is no specific eval-case statement for the EventCode it gets dropped from the table output. I am looking for a way to still return Pool and EventCode even if no EventNumber exists. OR, the lump all non-specified EventCodes into an "Other" category.
Any help is appreciated, Thanks in advance! JD
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just add a default value condition in the eval-case of yours, like this
(host=stwweb0* NOT host=stwweb0*I) sourcetype=WinEventLog:System SourceName="Microsoft-Windows-WAS" NOT 5186 | rex field=Message "(?i) pool (?P<Pool>[^ ]+)" |eval EventNumber=case(EventCode=5009 ,"5009 Terminated Unexpectedly",EventCode=5011,"5011 Communication Error",EventCode=5012,"5012 exceeded time limits during start up",EventCode=5013,"5013, exceeded time limits during shut down" ,EventCode=5014,"5014, internal error in its process management",EventCode=5074,"5074, worker process reached its allowed processing time limit",EventCode=5079,"5079, An administrator has requested a recycle",EventCode=5076,"5076, scheduled recycle time",EventCode=5138,"5138, failed to stop a listener channel for protocol 'http' in the allotted time",EventCode=5080,"5080, Recycled due to system settings change",EventCode=5010,"5010 Ping Timeout",1=1,"Other") |stats count by EventCode Pool EventNumber|eval Pool=Pool."-".count | stats list(Pool) as "Pool Count" by EventCode EventNumber
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That got it 1=1,"Google It".
Pasting my cleaned up version of this in case someone else needs to monitor App Pools the way we do.
sourcetype=WinEventLog:System SourceName="Microsoft-Windows-WAS" NOT 5186 NOT 5076 | rex field=Message "(?i) pool (?P<Pool>[^ ]+)"|eval Description=case(EventCode=5009 ,"Terminated Unexpectedly",EventCode=5011,"Communication Error",EventCode=5013,"Exceeded time during shut down" ,EventCode=5074,"Exceeded allowed processing time",EventCode=5079,"Administrator recycle",EventCode=5076,"Scheduled recycle time",EventCode=5080,"Pool settings changed",EventCode=5010,"Ping Timeout",1=1,"Google It..") |stats count by EventCode Description Pool
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Just add a default value condition in the eval-case of yours, like this
(host=stwweb0* NOT host=stwweb0*I) sourcetype=WinEventLog:System SourceName="Microsoft-Windows-WAS" NOT 5186 | rex field=Message "(?i) pool (?P<Pool>[^ ]+)" |eval EventNumber=case(EventCode=5009 ,"5009 Terminated Unexpectedly",EventCode=5011,"5011 Communication Error",EventCode=5012,"5012 exceeded time limits during start up",EventCode=5013,"5013, exceeded time limits during shut down" ,EventCode=5014,"5014, internal error in its process management",EventCode=5074,"5074, worker process reached its allowed processing time limit",EventCode=5079,"5079, An administrator has requested a recycle",EventCode=5076,"5076, scheduled recycle time",EventCode=5138,"5138, failed to stop a listener channel for protocol 'http' in the allotted time",EventCode=5080,"5080, Recycled due to system settings change",EventCode=5010,"5010 Ping Timeout",1=1,"Other") |stats count by EventCode Pool EventNumber|eval Pool=Pool."-".count | stats list(Pool) as "Pool Count" by EventCode EventNumber