Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Are you a member of the Splunk Community?
Sign in or Register with your Splunk account to get your questions answered, access valuable resources and connect with experts!
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Timechart to filter inactive buckets
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Timechart to filter inactive buckets
muralianup
Communicator
06-19-2018
09:00 AM
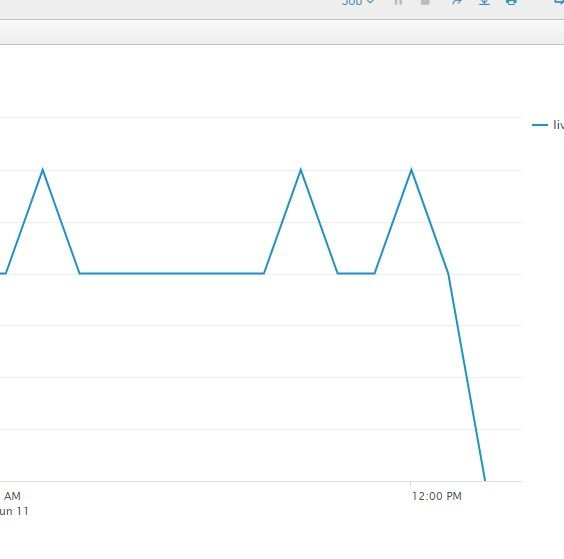
I need help with time chat query. Basically I want to display all the graph occurrences where the count hit 0 and stayed like that.
base search | timechart count by URL limit=100
That's where I am and there are some URL hits which were active at certain time then count was 0. I am searching through more than 1 URL and only want those whose count was zero after specific time.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
06-20-2018
06:18 AM
Hi @muralianup,
Try this
base search | timechart count by URL limit=100|untable _time URL count|where (count = 0 AND _time<your_time_filter)
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
06-25-2018
06:20 AM
Hi @muralianup,
Did this work for you?
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
Get Updates on the Splunk Community!
What the End of Support for Splunk Add-on Builder Means for You
Hello Splunk Community!
We want to share an important update regarding the future of the Splunk Add-on Builder ...
Solve, Learn, Repeat: New Puzzle Channel Now Live
Welcome to the Splunk Puzzle PlaygroundIf you are anything like me, you love to solve problems, and what ...
Building Reliable Asset and Identity Frameworks in Splunk ES
Accurate asset and identity resolution is the backbone of security operations. Without it, alerts are ...