Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Splunk Search
×
Join the Conversation
Without signing in, you're just watching from the sidelines. Sign in or Register to connect, share, and be part of the Splunk Community.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Timechart Cell value replace numeric value by cond...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
rishiaggarwal
Explorer
01-17-2016
06:24 PM
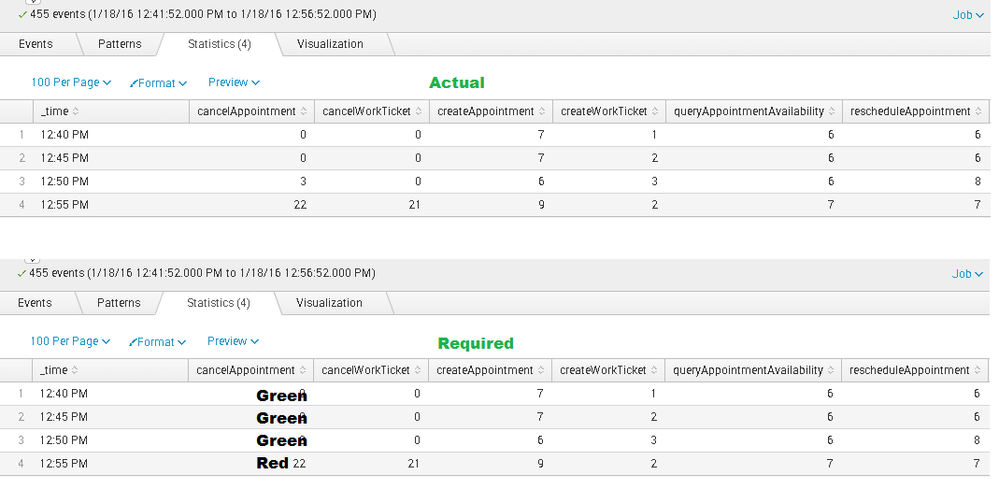
Hi All, i am newbie to Splunk and need an assistance in writing a splunk dashboard where i wish to replace the average transaction duration value with a range string. For eg. if the Transaction duration is between 0-6 sec, rather then displaying an actual average duration (number) it should display a text "Green".
Condition : 0-6 Green , 7-20 Amber, >20 Red
Draft Query is given below.
index=XXX_XXX sourcetype=XXX_YYY source=YXYX_YCYC
Search String
| transaction correlationId keepevicted=true
| timechart span=5m avg(duration) as response_health by activityName
| convert ctime(_time) as _time timeformat="%H:%M %p"
| fillnull
1 Solution
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
01-17-2016
09:03 PM
Try this
<your search>|untable _time activityName response_health|eval color=case(response_health==0 AND response_health<7,"Green",response_health> 6 AND response_health<21,"Amber" ,1=1,"Red")|xyseries _time activityName color
Instead of 1=1, you can provide response_heath>20 and give another default value in case the other three conditions are not matched.
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
renjith_nair
Legend
01-17-2016
09:03 PM
Try this
<your search>|untable _time activityName response_health|eval color=case(response_health==0 AND response_health<7,"Green",response_health> 6 AND response_health<21,"Amber" ,1=1,"Red")|xyseries _time activityName color
Instead of 1=1, you can provide response_heath>20 and give another default value in case the other three conditions are not matched.
---
What goes around comes around. If it helps, hit it with Karma 🙂
What goes around comes around. If it helps, hit it with Karma 🙂
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
rishiaggarwal
Explorer
01-17-2016
10:37 PM
Thanks a heap. This solution worked for me.
Get Updates on the Splunk Community!
App Platform's 2025 Year in Review: A Year of Innovation, Growth, and Community
As we step into 2026, it’s the perfect moment to reflect on what an extraordinary year 2025 was for the Splunk ...
Operationalizing Entity Risk Score with Enterprise Security 8.3+
Overview
Enterprise Security 8.3 introduces a powerful new feature called “Entity Risk Scoring” (ERS) for ...
Unlock Database Monitoring with Splunk Observability Cloud
In today’s fast-paced digital landscape, even minor database slowdowns can disrupt user experiences and ...