Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Search for Upload Activity to Unique Domains
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all,
I am trying to put together a search and stats table for users in our environment who have uploaded data to a domain where there has been not been any other upload activity to that domain in the last 7 days.
Operation="FileUploadedToCloud" - I'm working with fields such as user and targetdomain.
Any help is appreciated! Thanks!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A search like this I think will do it. (Set your search window to be last 7 days)
index=<origin_index> Operation="FileUploadedToCloud" earliest=-7d latest=now
| stats
count as upload_count,
earliest(_time) as earliest_upload_epoch,
latest(_time) as latest_upload_epoch
by user, targetdomain
| sort 0 -upload_count
| stats
dc(user) as dc_user,
list(user) as users,
min(earliest_upload_epoch) as earliest_upload_epoch,
max(latest_upload_epoch) as latest_upload_epoch,
list(upload_count) as upload_count,
sum(upload_count) as total_upload_count
by targetdomain
``` filter down results to only include domains where 1 user has uploaded in the specified search window ```
| where 'dc_user'==1
| convert
ctime(earliest_upload_epoch) as earliest_upload_timestamp,
ctime(latest_upload_epoch) as latest_upload_timestamp
| fields - *_upload_epoch
This should also return results if a single user has uploaded to a domain multiple times but is still the only user to upload to it in the last 7 days.
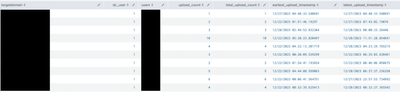
Resulting dataset would look something like this.
If scope needs to be narrowed to only 1 upload event by a user then you can additional filter to only return the events where 'total_upload_count'==1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A search like this I think will do it. (Set your search window to be last 7 days)
index=<origin_index> Operation="FileUploadedToCloud" earliest=-7d latest=now
| stats
count as upload_count,
earliest(_time) as earliest_upload_epoch,
latest(_time) as latest_upload_epoch
by user, targetdomain
| sort 0 -upload_count
| stats
dc(user) as dc_user,
list(user) as users,
min(earliest_upload_epoch) as earliest_upload_epoch,
max(latest_upload_epoch) as latest_upload_epoch,
list(upload_count) as upload_count,
sum(upload_count) as total_upload_count
by targetdomain
``` filter down results to only include domains where 1 user has uploaded in the specified search window ```
| where 'dc_user'==1
| convert
ctime(earliest_upload_epoch) as earliest_upload_timestamp,
ctime(latest_upload_epoch) as latest_upload_timestamp
| fields - *_upload_epoch
This should also return results if a single user has uploaded to a domain multiple times but is still the only user to upload to it in the last 7 days.
Resulting dataset would look something like this.
If scope needs to be narrowed to only 1 upload event by a user then you can additional filter to only return the events where 'total_upload_count'==1
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is perfect. Thank you!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If your problem is resolved, then please click an "Accept as Solution" button to help future readers.
If this reply helps you, Karma would be appreciated.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Search over the last 7 days and count entries by target domain. Filter out anything with a count greater than 1.
index=foo Operation=FileUploadedToCloud user=* targetdomain=* earliest=-7d
| stats count, values(*) as * by targetdomain
| where count=1If this reply helps you, Karma would be appreciated.