Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Search event is not providing output for field...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have created http event with below command:
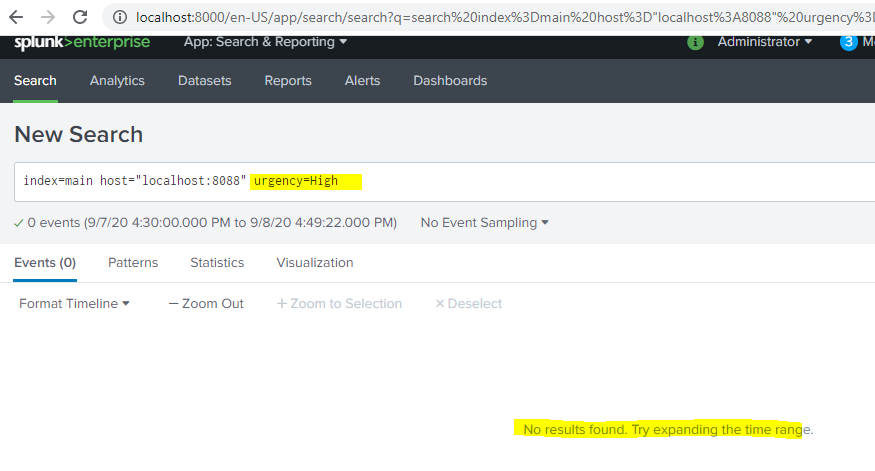
This data is visible on splunk enterprise. Now we are trying to search this event using criteria as Urgency = High . but it didn't return any event.
We tried using curl command still same result. Can you suggest what could be the issue?
C:\Users\terminal>curl -k -u username:Password https://localhost:8089/services/search/jobs -d output_mode="json" -d search="search index=main urgency=high"
{"sid":"1599554403.2242"}
C::\Users\terminal>curl -k -u username:Password :username:Password https://localhost:8089/services/search/jobs/1599554403.2242/events --get -d output_mode="json"
output:
"preview":false,
"init_offset":0,
"messages":[ ],
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, you need handle search criteria differently based on how you would like to project your results in reports or dashboards.
and also, I think you are adding sourcetype also inside the event attribute while constructing data for HTTP event collector. if you use sourcetype field separately as event then you don't see it in events but you see new field sourcetype because this is meta field.
curl -k -H "Authorization: Splunk 12345678-1234-1234-1234-1234567890AB" https://mysplunkserver.example.com:8088/services/collector/event -d '{"sourcetype": "my_sample_data", "event": "http auth ftw!"}'
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
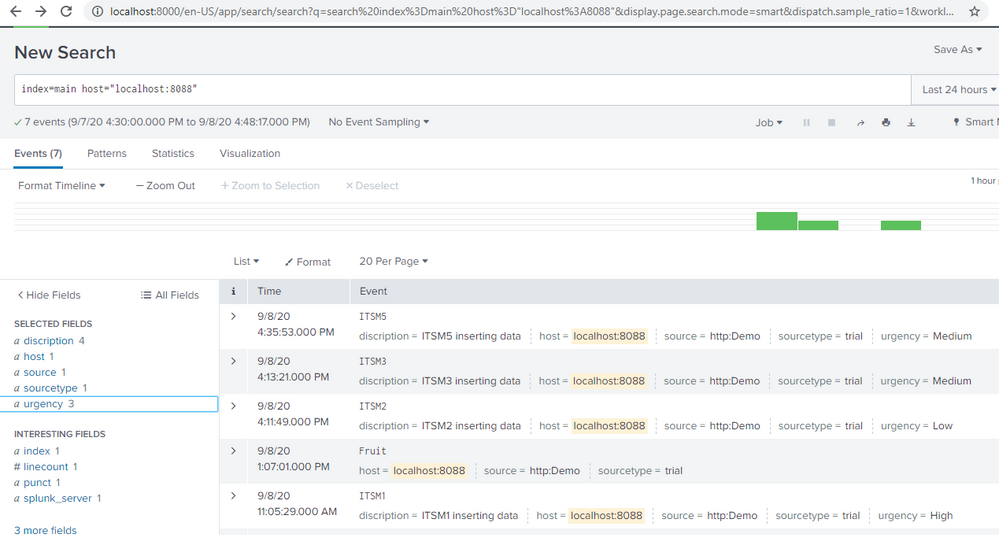
Adding screenshots for events created and search result. Fields are extracted but result is not listed.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
How did you add urgency=High to your search? Typing it in or selecting it from the list of values and adding it to the search?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@thambisetty @ITWhisperer We tried both ways. In case of selecting search criteria from suggested drop down list also we are getting 0 results. Is there any search specific for HTTP event collector where event is created with json body provided as :
"sourcetype":"trial",
"event":"ITSM2",
"fields":
{ "discription":"ITSM2 inserting data",
"urgency":"Low"
}}
"event":
{ "discription":"ITSM2 inserting data",
"urgency":"Low"
}}
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
yes, you need handle search criteria differently based on how you would like to project your results in reports or dashboards.
and also, I think you are adding sourcetype also inside the event attribute while constructing data for HTTP event collector. if you use sourcetype field separately as event then you don't see it in events but you see new field sourcetype because this is meta field.
curl -k -H "Authorization: Splunk 12345678-1234-1234-1234-1234567890AB" https://mysplunkserver.example.com:8088/services/collector/event -d '{"sourcetype": "my_sample_data", "event": "http auth ftw!"}'
If this helps, give a like below.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
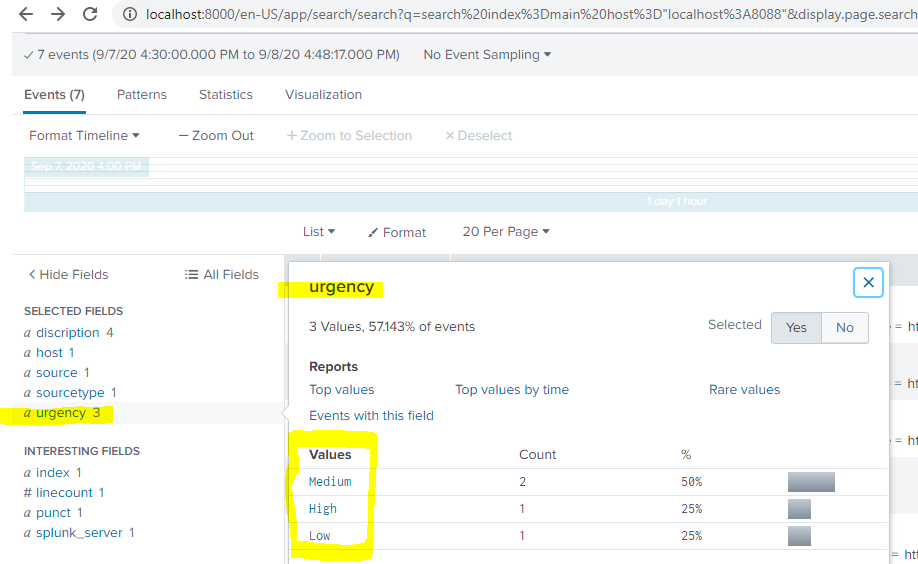
- you are trying to filter events with Urgency = High and you are getting 0 results, that's because fields are not extracted from the event. if the field is extracted from the event you could see same from fields window left side.Splunk fields
- also same reason your search is matched with 0 results, you should also specify timerange.
-------------------------------
Give a thumps if it solves your problem.
If this helps, give a like below.