Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: SPLUNK Search derived from Stream app produces...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi there, when I run this search:
index=* source=stream:Splunk_IP | rex field=src_ip "(?<src1>.*)\.(?<src2>.*)\.(?<src3>.*)\.(?<src4>.*)" | where src1 NOT null | rex field=dest_ip "(?<dest1>.*)\.(?<dest2>.*)\.(?<dest3>.*)\.(?<dest4>.*)" | where dest1 NOT null | eval source_ip=round(src1+exact(src2*.001), 3) | eval destination_ip=round(dest1+exact(dest2*.001), 3) | eventstats sum(sum(bytes)) as bytes by source_ip, destination_ip | stats latest(source_ip), latest(destination_ip), sum(count) by bytes | rename latest(source_ip) as "Source IP", latest(destination_ip) as "Destination IP", sum(count) as "Flows", bytes as "Bytes", sourcetype as "Sourcetype"
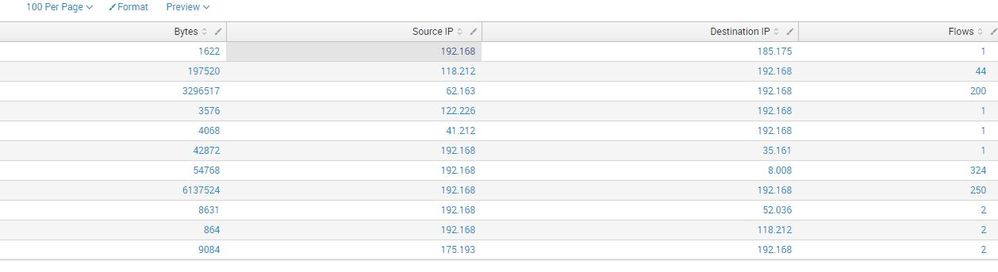
It produces this result:
As you'll notice the other half of source and destination ipaddresses are missing.
Is this: ????
- Because the flow data doesn't arrive properly in SPLUNK
- The stream app needs more configuring
- Search syntax is wrong
I'd highly appreciate an answer on this.
Thanks in advance!
Erik
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
In these commands:
| eval source_ip=round(src1+exact(src2*.001), 3) | eval destination_ip=round(dest1+exact(dest2*.001), 3)
you try to concatenate only two parts of IP (src1 and src2). No wonder, that half of IP is missing. Substitute these evals with:
| eval source_ip = src1 + "." + src2 +"." + src3 + "." + src4 | eval destination_ip = dest1 + "." + dest2 + "." + dest3 + "." + dest4
By the way, are you sure you need such conversion? I'm guessing, src_ip and dest_ip contains the whole and correct IP addresses, and you can use them instead of source_ip and destination_ip.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Anyone?
WIth advice?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've now this search:
index=* source="stream:*" source="stream:fortistream"
|table timestamp, src_ip, dest_ip, ,dest_port, sum(bytes_in), sum(bytes_out)
But how do I make sure the values of scr_ip and dest_ip belong together within the same data flow?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Basically this will work for me:
index=* source="stream:*" source="stream:fortistream"
|table timestamp, src_ip, dest_ip, ,dest_port, sum(bytes_in), sum(bytes_out)
So what do I need this crazy search that comes with the stream app datamodel for then?
Why did they set it up like this?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi!
In these commands:
| eval source_ip=round(src1+exact(src2*.001), 3) | eval destination_ip=round(dest1+exact(dest2*.001), 3)
you try to concatenate only two parts of IP (src1 and src2). No wonder, that half of IP is missing. Substitute these evals with:
| eval source_ip = src1 + "." + src2 +"." + src3 + "." + src4 | eval destination_ip = dest1 + "." + dest2 + "." + dest3 + "." + dest4
By the way, are you sure you need such conversion? I'm guessing, src_ip and dest_ip contains the whole and correct IP addresses, and you can use them instead of source_ip and destination_ip.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks! When I convert the syntax like this:
index=* source=stream:Splunk_IP | rex field=src_ip "(?<src1>.*)\.(?<src2>.*)\.(?<src3>.*)\.(?<src4>.*)" | where src1 NOT null | rex field=dest_ip "(?<dest1>.*)\.(?<dest2>.*)\.(?<dest3>.*)\.(?<dest4>.*)" | where dest1 NOT null | | eval source_ip = src1 + "." + src2 +"." + src3 + "." + src4 | eval destination_ip = dest1 + "." + dest2 + "." + dest3 + "." + dest4 | eventstats sum(sum(bytes)) as bytes by source_ip, destination_ip | stats latest(source_ip), latest(destination_ip), sum(count) by bytes | rename latest(source_ip) as "Source IP", latest(destination_ip) as "Destination IP", sum(count) as "Flows", bytes as "Bytes", sourcetype as "Sourcetype"
It produces an error message: Error in 'SearchParser': Missing a search command before '|'. Error at position '235' of search query 'search index=* source=stream:Splunk_IP | rex field...{snipped} {errorcontext = OT null | | eval sour}'.
You'd say you don't need the source_ip, however it's part of the data model. If I try search on src_ip I don't get any data.. Or.. I'm doing wrong search, what would be the search syntax then?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is happening because you are using round function. can you try to remove it?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I wonder why they even use the round function on an ipaddress!? 🙂
Anyway, if I remove it I mess up the syntax completely..