Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Regex not accepted when searching
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
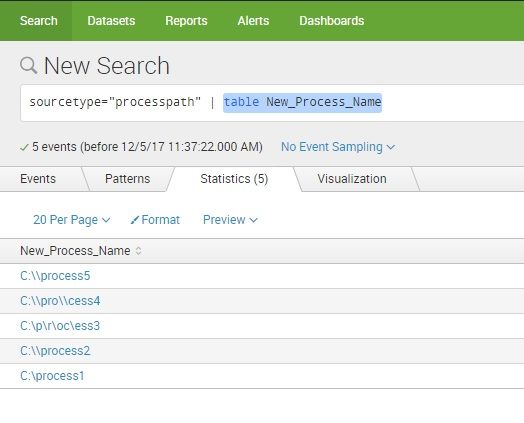
Hi guys,
I am trying to get a regex to just match if a process has been run from the C drive, root folder.
I tried the following regex
regex New_Process_Name!="C:\\+[^\\\]+$"
but I still get all processes. The logic is simple: match only if there is no further "\" after "C:\".
What am I doing wrong?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @robettinger,
Please try below query, in below query first lines generating dummy data. Replace _raw in rex command with actual field name in which your processname stores.
| makeresults
| eval _raw="C:\abc.exe"
| append [ | makeresults | eval _raw="C:\abc\xyz.exe"]
| append [ | makeresults | eval _raw="C:\abc\pqr\xyz.exe"]
| rex field=_raw "(?m)C:[\\\](?<process>.*?[\\\].*)$"
| where isnull(process)
I hope this helps.
Thanks,
Harshil
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
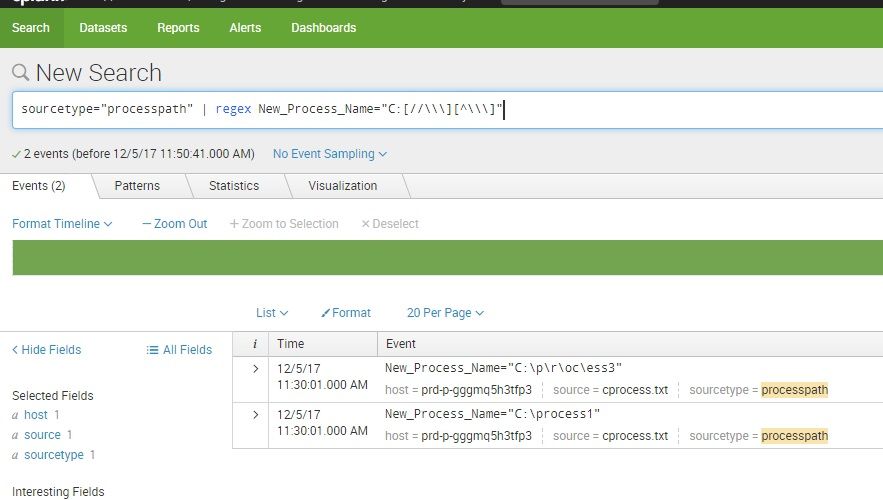
I think you had the right idea, but I'm not a fan of escaping backslashes with rex/regex. Try this:
| regex New_Process_Name="^C:\x5c[^\x5c]+$"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @robettinger,
Please try below query, in below query first lines generating dummy data. Replace _raw in rex command with actual field name in which your processname stores.
| makeresults
| eval _raw="C:\abc.exe"
| append [ | makeresults | eval _raw="C:\abc\xyz.exe"]
| append [ | makeresults | eval _raw="C:\abc\pqr\xyz.exe"]
| rex field=_raw "(?m)C:[\\\](?<process>.*?[\\\].*)$"
| where isnull(process)
I hope this helps.
Thanks,
Harshil
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmmmm. Thank you! That is some improvement, but not quite yet what I had in mind .... Let me paste my entire query:
index=win_sec EventCode=4688 earliest=-1h@h latest=now New_Process_Name="C:\\Temp*" OR New_Process_Name="*AppData\\Local\\Temp*" OR #########
| eval Account_Name=mvindex(Account_Name,0)
| eval Account_Domain=mvindex(Account_Domain,0)
| table _time, host, Account_Domain, Account_Name, app, New_Process_Name
The ##### part should be where New_Process_Name is something like "C:\xxx.xxx" but not "C:\xxx\xxx.xxx"
Your query makes sense but it's also renaming the New_Process_Name field which is not my intention ... Any ideas?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
ok, can you please try this
| makeresults
| eval New_Process_Name="C:\abc.exe"
| append [ | makeresults | eval New_Process_Name="C:\abc\xyz.exe"]
| append [ | makeresults | eval New_Process_Name="C:\abc\pqr\xyz.exe"]
| append [ | makeresults | eval New_Process_Name="C:\Temp\xyz.exe"]
| append [ | makeresults | eval New_Process_Name="C:\abc\AppData\Local\Temp\xyz.exe"]
| rex field=New_Process_Name "(?m)(?<process>C:\\\(?!Temp|.*\\\AppData\\\Local\\\Temp\\\).*?\\\.*)$"
| where isnull(process)
So your query will be
index=win_sec EventCode=4688 earliest=-1h@h latest=now
| rex field=New_Process_Name "(?m)(?<process>C:\\\(?!Temp|.*\\\AppData\\\Local\\\Temp\\\).*?\\\.*)$"
| where isnull(process)
| eval Account_Name=mvindex(Account_Name,0)
| eval Account_Domain=mvindex(Account_Domain,0)
| table _time, host, Account_Domain, Account_Name, app, New_Process_Name
EDIT: Updated the query
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content