Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Re: Regex
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Regex- Help with extracting field
Can someone please help me in extracting the field Specific_DL_Testing from the below sample log.
instance of the "\Specific_DL_Testing" task.
The output should be Specific_DL_Testing
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I have used the above expression but its not extracting the field.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Here is a runanywhere example of it working
| makeresults
| eval _raw="instance of the \"\\Specific_DL_Testing\" task."
| rex "instance of the \"\\\(?<task>[^\"]+)\" task."If it is not working for you, please provide example events and the SPL you are using (preferably in code blocks </> like the example above to prevent information being lost due to formatting
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Task Scheduler terminated "{8878FDRGSGS-8cde-1234-123456789}" instance of the "\Specific_DL_Testing" task.
Please try on this event
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| makeresults
| eval _raw="Task Scheduler terminated \"{8878FDRGSGS-8cde-1234-123456789}\" instance of the \"\\Specific_DL_Testing\" task."
| rex "instance of the \"\\\(?<task>[^\"]+)\" task."- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I see you are checking for "\\Specific_DL_Testing\"
Can you try for "\Specific_DL_Testing\"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
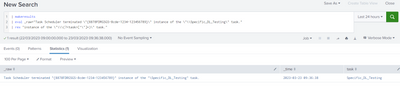
I am not checking for "\\Specific_DL_Testing\" - this is part of the eval command to create the sample _raw field in line with what you say is your event
As you can see from the _raw field in the screenshot, the event matches what you said you event was.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Getting error :- Error in 'rex' command: Encountered the following error while compiling the regex '\instance of the "\(?<task>[^"]+)" task.': Regex: unrecognized character follows \.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I missed a backslash
| rex "instance of the \"\\\(?<task>[^\"]+)\" task."- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
| rex "instance of the \"\\(?<task>[^\"]+)\" task."