Join the Conversation
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- REX issue, quite an interesting one, potential bug...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
REX issue, quite an interesting one, potential bug?
Just wondering if anyone has ever seen this before?
This is the data I’m extracting from:
"Classic,Audit Failure",11/14/2016 9:32:27 AM,AD FS Auditing,516,-3,"The following user account has been locked out due to too many bad password attempts. Additional Data Activity ID: 00000000-0000-0000-0000-000000000000 User: sausages\Abel.Caine Client IP: 103.1.1.1,10.1.1.1 nBad Password Count: 4 nLast Bad Password Attempt: 11/14/2016"
I’m trying to extract the bad password count.
By all means, this should work:
| rex "Password Count: (?P[^ \n]+)"
But it appears that Splunk sees the string ‘Count’ as a command, not just a string.
I get the total ‘count’ of those fields it finds.
I’ve tried escaping it, using “\s{1}\w{6}” and a load of others things.
Seen this before?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This works fine:
... | rex "Password Count:\s*(?<Count>\d+)"
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi mrgibbon 😉
works like a charm on Splunk 6.5.0:
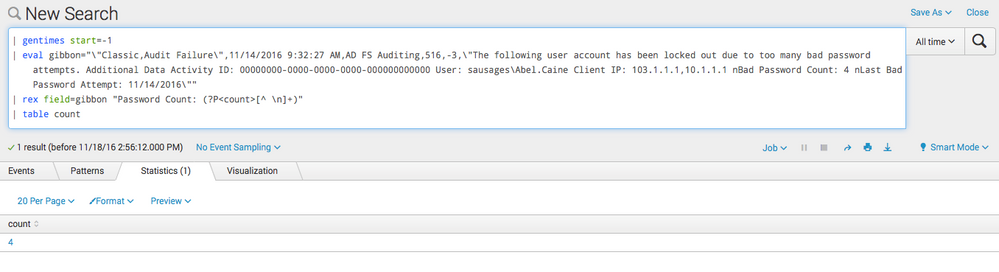
| gentimes start=-1
| eval gibbon="\"Classic,Audit Failure\",11/14/2016 9:32:27 AM,AD FS Auditing,516,-3,\"The following user account has been locked out due to too many bad password attempts. Additional Data Activity ID: 00000000-0000-0000-0000-000000000000 User: sausages\Abel.Caine Client IP: 103.1.1.1,10.1.1.1 nBad Password Count: 4 nLast Bad Password Attempt: 11/14/2016\""
| rex field=gibbon "Password Count: (?P<count>[^ \n]+)"
| table count
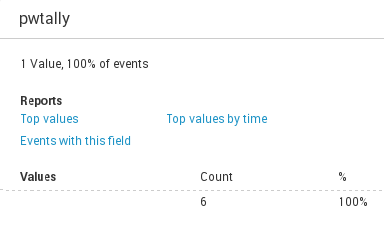
Here is the result:
Can you please add the complete search you are running?
cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hmm, Im using 6.5.0.
Might be something quirky in the way the event is ingested, its only ADFS logs though, fairly std.
index=adfs "Event ID"=403 OR "Event ID"=516 NOT "Audit Success"
| rex "blah.internal\\\(?P[^ \n]+)"
| rex "Activity ID: (?P[^\n \"]+)"
| rex "((\\d{1,3}\.\\d{1,3}\.\\d{1,3}\.\\d{1,3}).+?(?P\\d{1,3}\.\\d{1,3}\.\\d{1,3}\.\\d{1,3}))"
| rex "nBad Password\s{1}\w{5}\:\s(?P[^ \n]+)"
| rex "nLast Bad Password Attempt: (?P[^\"]+)"
This is just one variation I have tried, of course I have tried the most basic one I listed first.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why the \n? Seems to me you only need [^ ]+
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I added it in as when I view the event that number is actually below the leading text, like this:
nBad Password Count:
4
So I added it in to cope with that, but if you copy out the event its directly following the colon and a space. I have tried without it, still the same result.
Thanks
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Also, I want the value of the field, not the count of those fields.
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi mrgibbon, you know how to reach me - Can you send some sample data and the search and I will have a look at it 😉 Cheers, MuS
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you use the code function so the named capturing groups are still in the search, please? 🙂