Are you a member of the Splunk Community?
- Find Answers
- :
- Using Splunk
- :
- Splunk Search
- :
- Query with Thousands IDs in searche whit OR
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark Topic
- Subscribe to Topic
- Mute Topic
- Printer Friendly Page
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello, i need help.
I have 6500 IIN (like id) and put this id to lookup then tried search: index=alfa [|inputlookup IIN_oleg.csv |rename IIN as search | fields search]
They given result only for one firs IIN in lookup.
If i search whit out lookup just 10 IIN whit "OR" the give me 10 result
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this,
index=alfa [|inputlookup IIN_oleg.csv |rename IIN as search | table search | format "(" "(" "AND" ")" "OR" ")"] - Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One more thing I observed in my instance. Incase if may OR conditions the search it self is getting break.. So can you please run your search and check the job inspect? Is that any error?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
start search index=alfa [|inputlookup IIN_oleg.csv |rename IIN as search | fields search]
search.log
08-05-2021 12:36:55.531 ERROR LookupProviderFactory - Must specify one or more lookup fields.
08-05-2021 12:36:54.743 INFO SearchParser - PARSING: search index=alfa [|inputlookup IIN_oleg.csv |rename IIN as search | fields search] |
08-05-2021 12:36:55.531 ERROR LookupProviderFactory - Must specify one or more lookup fields. 08-05-2021 12:36:55.531 ERROR AutoLookupDriver - Could not load lookup='LOOKUP-cisco_asa_ids_lookup' reason='Error in 'lookup' command: Must specify one or more lookup fields.' 08-05-2021 12:36:55.531 ERROR LookupProviderFactory - Must specify one or more lookup fields. 08-05-2021 12:36:55.531 ERROR AutoLookupDriver - Could not load lookup='LOOKUP-cisco_asa_intrusion_severity_lookup' reason='Error in 'lookup' command: Must specify one or more lookup fields.'
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
i can not find in logs why the thake only firs value in lookup. I think the problem in query
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Try this,
index=alfa [|inputlookup IIN_oleg.csv |rename IIN as search | table search | format "(" "(" "AND" ")" "OR" ")"] - Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
cool
Glad to help you 🙂
!! Happy Splunking !!
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
No, not give any result 😔
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can you please try this?
index=alfa
| rex field=_raw "parameter\sname=\\\\\"(?<name>.*)\\\\\"\svalue=\\\\\"(?<value>\d+)\\\\\"\/>"
| where name="IIN"
| stats count by value
KV
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
we dont have field like IIN in index data
index=alfa | rex field=_raw "parameter\sname=\\\\\"(?<name>.*)\\\\\"\svalue=\\\\\"(?<value>\d+)\\\\\"\/>" | where name="IIN" | stats count by value
Result 0
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
OK
Then how you want to map with IIN_oleg.csv?
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
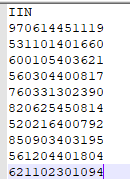
lookup data
data in index
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks @Dmitriy
Are you able to extract name and value fields from events?
index=alfa name="IIN" | stats count by value
Is this query working for you?
If Not can you please share sample _raw event, so I can help you on extraction also.
KV
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark Message
- Subscribe to Message
- Mute Message
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you have same field name then you can try like this.
index = alfa
| lookup IIN_oleg.csv IIN output IIN as IIN_1
| where isnotnull(IIN_1)KV